
Web Developers
Palo Alto Networks investigated and documented the malware in the US, writing:
XcodeGhost’s primary behavior in infected iOS apps is to collect information on the devices and upload that data to command and control (C2) servers. The malware has exposed a very interesting attack vector, targeting the compilers used to create legitimate apps. This technique could also be adopted to attack enterprise iOS apps or OS X apps in much more dangerous ways.
The offending malware was hidden in hacked versions of Xcode, Apple’s software platform for developing Mac OS X and iOS applications, which was hosted on servers operated by Chinese search engine Baidu. Hackers had replaced Apple’s clean code with code containing the Trojan horse, and the tools were inadvertently used by many developers, whose apps were then approved for hosting and sale in Apple’s App Store. Palo Alto Networks downloaded several of these Xcode installers and found that all versions of Xcode from 6.1 to 6.4 were infected. The company also verified that extra files were added to the Xcode download. (The latest update of Xcode is version 7.)
Apple’s Xcode development software is hosted on many servers in China in order to speed up its download time, particularly from Apple’s overseas servers. China has relatively slow Internet speeds, ranking 84th globally and below average for the region, as seen in the chart below:
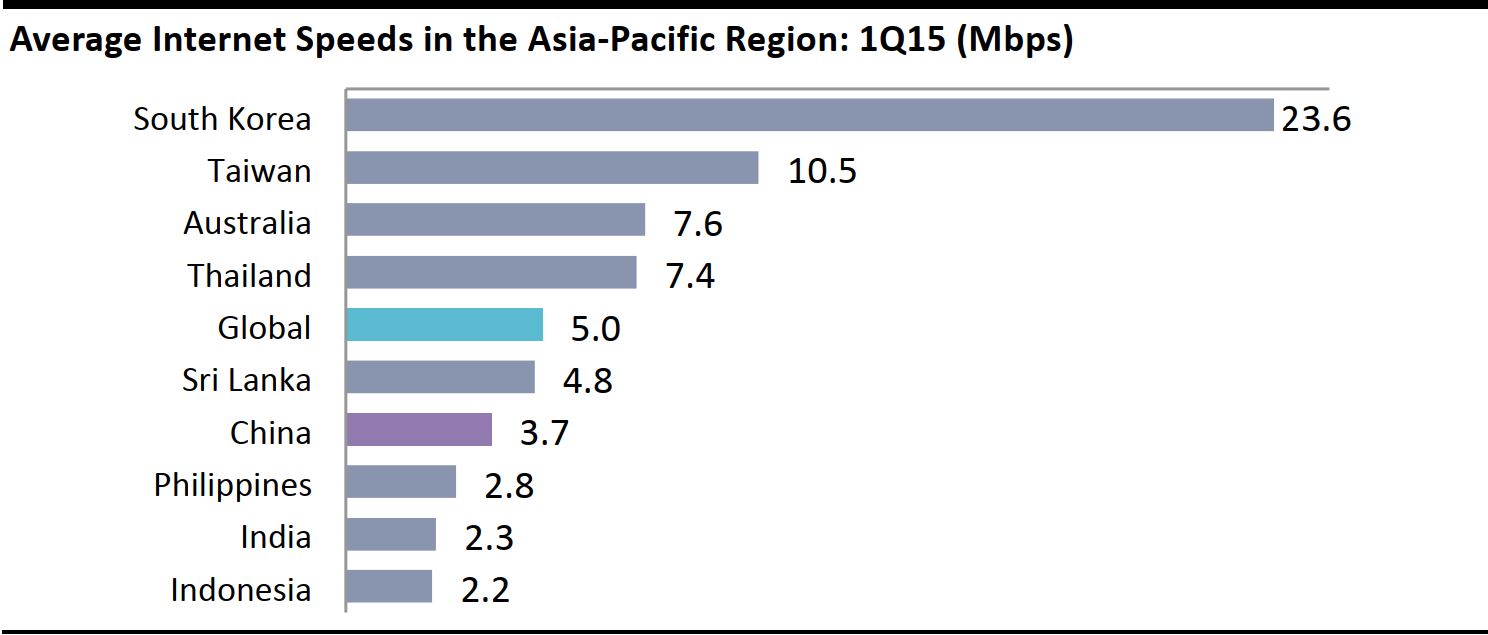

Source: Akamai
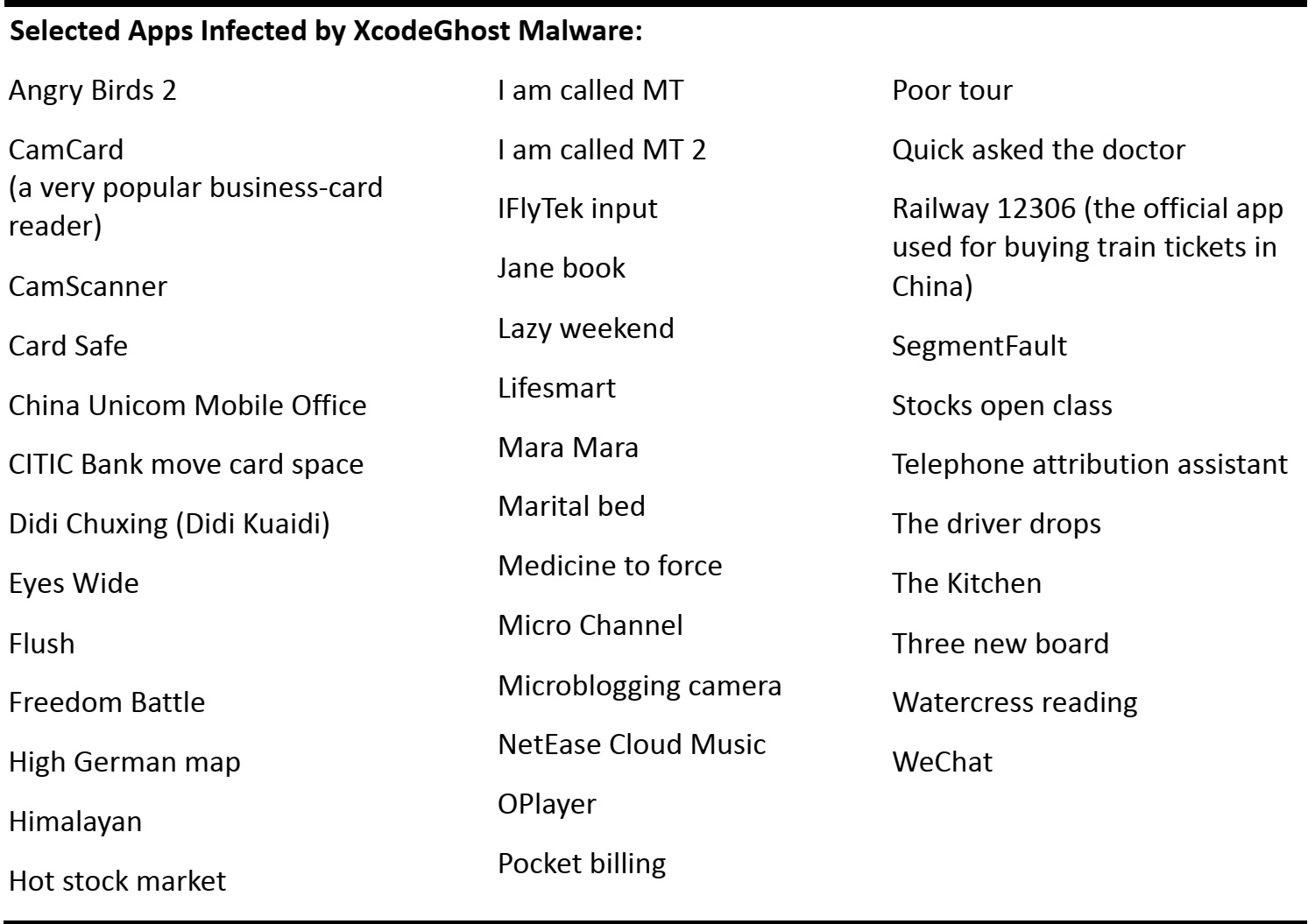
Some estimate that as many as 300 apps were affected by the XcodeGhost malware. Below is a translated list of 38 apps that were infected, including several prominent ones: WeChat (version 6.2.5), Didi Kuaidi’s taxi-hailing app (versions 4.0.0.6–4.0.0.0), NetEase Cloud Music (version 2.8.3) and the I am called MT game app (version 5.0.1), which was the top revenue-generating app on Apple’s App Store in China in 2013, according to App Annie.