Executive Summary
Ever since humans began treasuring objects of value, there have been individuals who have wanted to steal or damage those objects. In our current era, the Information Age, data represent many of our objects of value. PC viruses have existed essentially since the advent of the PC. And as the PC’s capabilities have increased over time, following Moore’s law, so, too, has the value of the data residing on them, making them an attractive target for criminals.
The invention of the Internet has made the world flat, enabling us to shop and make purchases from faraway countries. At the same time, it has enabled invisible criminals at home and abroad to sometimes break into our PCs and take our data, lock up our devices in exchange for ransom, or cause other types of havoc.
At one time, cybersecurity simply consisted of protecting computers from viruses and malware that could be hidden on a floppy disk. Now, computer users are vulnerable to picking up such maladies while browsing the web, using a mobile phone, logging into a free Wi-Fi service or even plugging in a USB stick they might have found.
Unfortunately, the Internet has become a darker place. In the past, teenage hackers might have broken into computer systems in order to demonstrate their abilities and cause minor chaos, but now, organized criminal gangs are colluding with state-sponsored hacking groups to engage in larceny, extortion, and corporate and private espionage. Moreover, some miscreants are now invading computers and encrypting the hard drive, threatening to release it only in exchange for a hefty ransom payment made in untraceable bitcoin.
For both individuals and enterprises, it is a struggle to keep the bad actors at bay. They are relentless and tireless, and all it takes is one person clicking on the wrong email link to let them in. Cyberattacks are largely enabled by the human element—by our own apathy, inattention to detail or lack of vigilance. Hackers often get in when IT managers do not apply software updates or patches or do not heed the yellow and red flags generated by security monitors. And many IT teams do not have a plan in place to deal with break-ins, which are almost inevitable. The burden of cybersecurity falls on all of us: to keep cybercriminals out, we must stay on top of our game and not doze off.
Enter the good guys, offering cybersecurity solutions. Just as we have to buy locks to protect our homes, IT managers have to arm themselves with a suite of tools to fend off network invasions, or at least minimize their effects. The negative PR and business consequences that can result from a network incursion are just too great a risk to not deal with the cybersecurity threat proactively, as many retailers and government agencies have painfully learned.
In this report, we provide a general overview of cybersecurity, the different types and methods of cyberattacks, and many details about the industry and the companies that are working to keep our devices and networks safe from cybercriminals.
About This Deep Dive
Fung Global Retail & Technology is publishing its
Deep Dive: An Introduction to Cybersecurity in three installments.
The Executive Summary outlines the growth of the Information Age and the advent of the Internet, the benefits of which have been tested often by corresponding developments in computer viruses and malware. Recently, though, the Internet has become a significantly darker place. The bad actors online used to be mostly teenage hackers, but they are being replaced by organized crime syndicates and state-sponsored hackers with much bigger criminal ambitions. The good guys have labored to keep pace with the cybercriminals, and a rich cybersecurity industry has emerged, with a large number of companies specializing in the various aspects of online security.
Part One: Introduction and Components of Cybersecurity
The growing interconnectedness of computers and increasing use of the Internet make computers an irresistible target for cybercriminals. As Internet usage has increased and hacking tools have become more accessible, the number of reported cyberattacks has risen. The cat-and-mouse game between virus developers and antivirus software makers continued relatively peacefully until about 2010, when the balance between hackers and defenders was severely altered.
In 2013, the National Institute of Standards and Technology defined five categories in a framework for reducing cyber-risks to infrastructure: identification, protection, detection, response, and recovery.
Part Two: Components of an Advanced Attack, Characteristics of an Advanced Persistent Threat, and Types of Attacks and Hackers
The term “APT” refers to an advanced persistent threat, a cyberattack in which an unauthorized person gains and maintains access to a network for an extended period of time. Recent APTs have targeted enterprises.
APTs can take a number of forms, including malware, spam, botnet and ransomware attacks, and hackers can take advantage of vulnerabilities in systems, such as the use of weak or common passwords.
Types of hackers include script kiddies and white, black, gray, green, red and blue hats.
Part Three: New Threats/Threat Vectors, Markets and Cybersecurity Companies
The number and kinds of cyberthreats continue to grow and evolve due to advances in technology that benefit both attackers and defenders.
Market intelligence firm IDC forecasts that global spending on cybersecurity will increase at an 8.3% CAGR between 2016 and 2020, growing from $73.6 billion to $101.6 billion. This growth rate is more than double the 3.3% CAGR that IDC forecasts for worldwide IT product revenue from 2015 through 2020.
The Fung Global Retail & Technology team hopes that you will find this
Deep Dive interesting and informative and that it will help you protect your enterprise against cybersecurity threats!
New Threats/Threat Vectors
The number and kinds of cyberthreats continue to grow and evolve due to advances in technology that benefit both attackers and defenders.
Moore’s Law/Quantum Computing
Computing power is steadily increasing, which continually undermines the safety of current encryption algorithms. Moore’s law is commonly understood to mean that computing power doubles every two years, but Moore’s observation concerned the density of transistors on an integrated circuit: he originally observed that the number of transistors on such a circuit was doubling every 18 months, not that computing power itself was doubling at that rate. However, there is a correlation between transistor density and computing power.
When 512-bit RSA keys were first created in 1999, it took a supercomputer or an array of then state-of-the-art computers seven months to break them. Today, it takes $75 and four hours on Amazon’s Elastic Compute Cloud service to break a 512-bit RSA code.
Quantum computers theoretically do not use binary ones and zeros; rather, they use quantum bits, which can be the superposition of different states. Google claimed that its D-Wave quantum computer can solve certain problems 100 million times faster than an ordinary computer can. Furthermore, a quantum computer could possibly break long encryption keys in a fraction of the time currently required.
The IoT
The explosion of the IoT has corresponded with an explosion of new hardware platforms—many of which have been designed with utility, rather than security, in mind, making them easy targets for hackers. Cisco initially estimated that 50 billion devices would be connected to the IoT by 2020, but estimates have become more conservative over time. As of March 2016, research firm IHS estimated that 30.7 billion IoT devices would be connected in 2020.
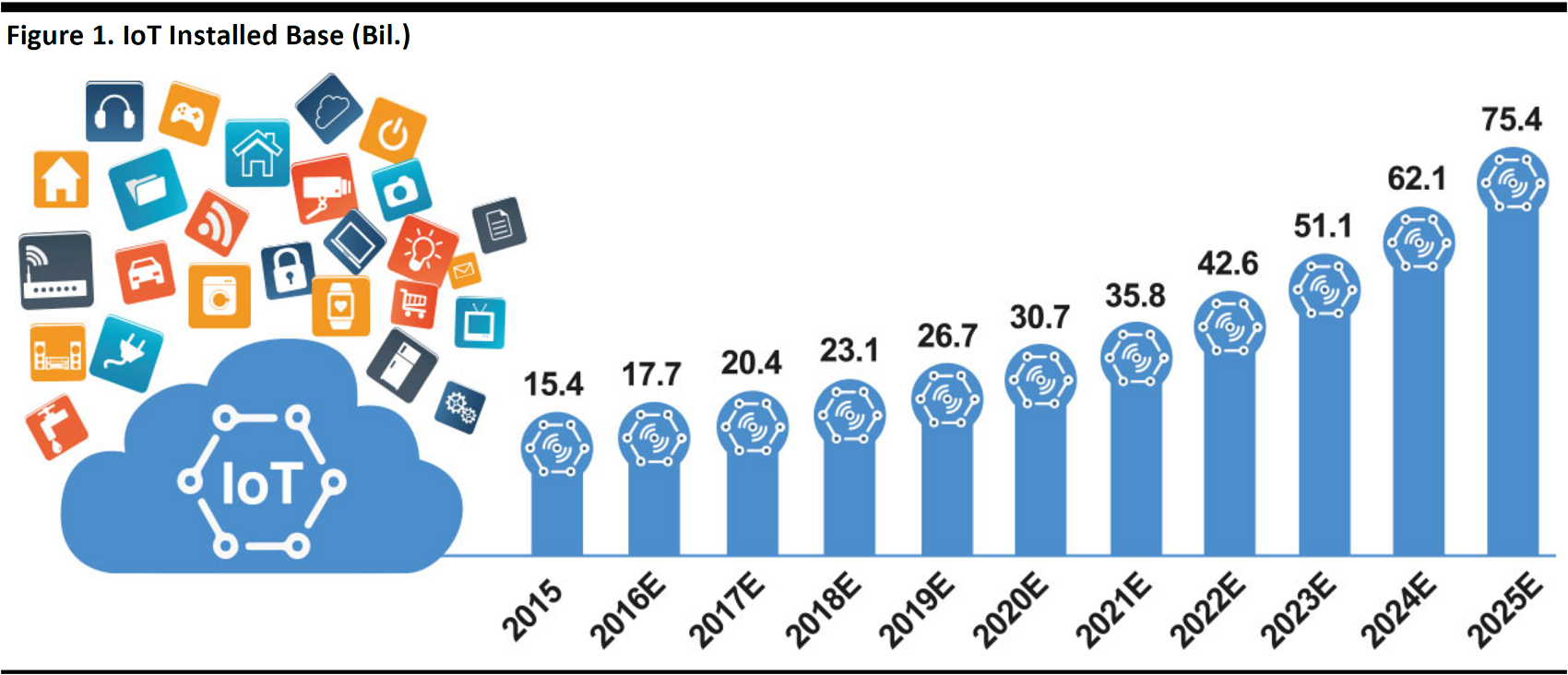
Projections as of March 2016
Source: IHS
Although we are only in the early stages of the boom in IoT devices, there have already been several notable instances of IoT hacking:
- In 2014, security researchers gained access and inserted malicious code into the control software of a Jeep SUV through its diagnostic port. The researchers were able to control the air conditioning, music, steering, brake and transmission systems, among others.
- In October 2016, the Mirai botnet unleashed a DDoS attack emanating from 145,000 infected IoT devices, including home security cameras and DVRs in homes and offices. The botnet attacked Dyn, a large Internet domain name server, which caused outages at Twitter, Spotify, Reddit, The New York Times, Pinterest, PayPal and other major companies’ websites.
- Most recently, vulnerabilities were discovered in the Ring wireless doorbell that were allowing packets of audio data to be sent to Chinese Internet giant Baidu at random intervals.
Mobile Devices
The explosion in the capabilities and use of mobile devices has greatly multiplied the number of machines that can be attacked or serve as platforms for invading enterprise systems. Market intelligence firm IDC has forecast smartphone shipments through 2021, as shown in the figure below.
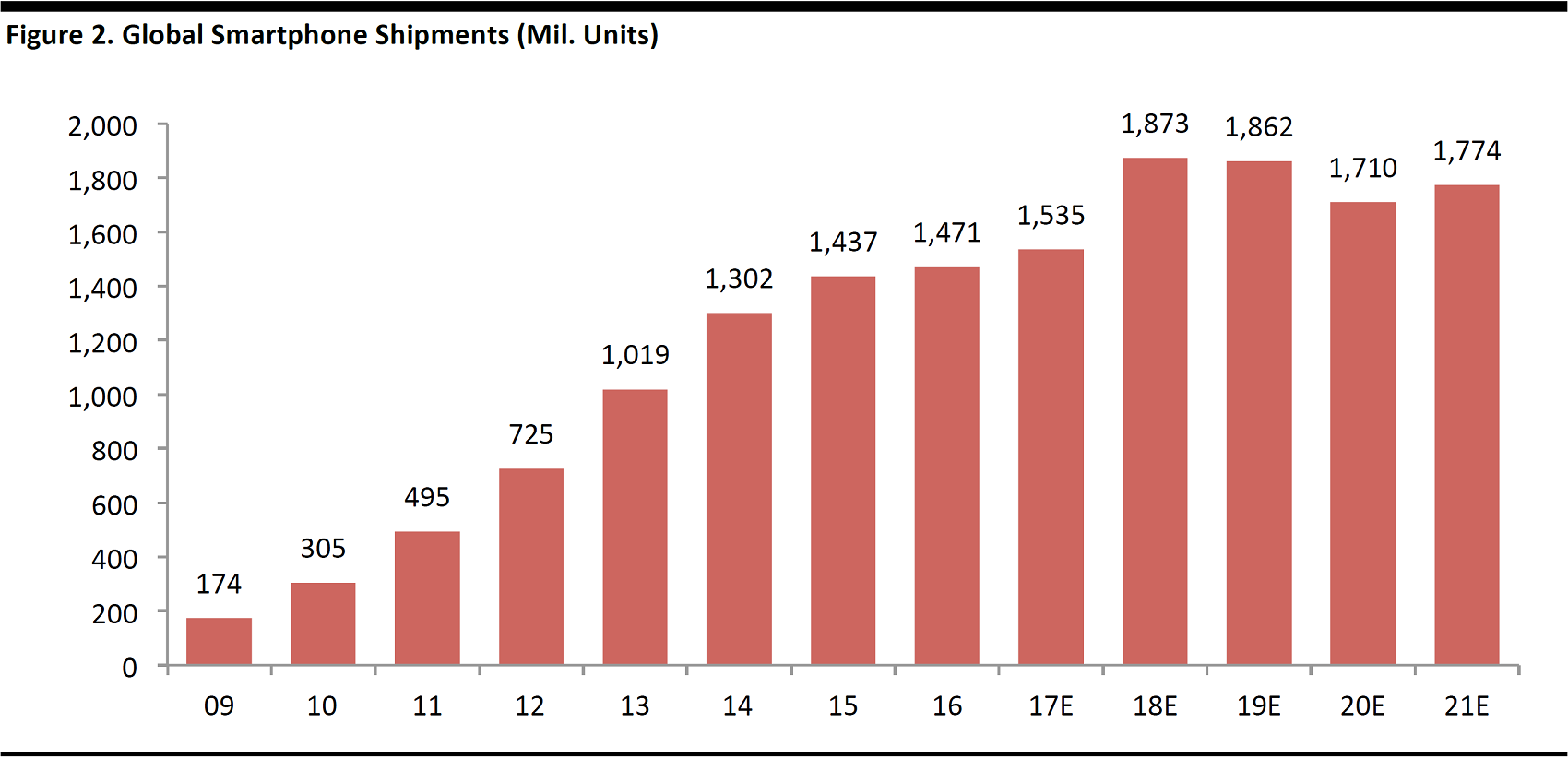 Forecasts as of March 2017
Source: IDC
Forecasts as of March 2017
Source: IDC
The amount of mobile malware has grown alongside the increase in smartphone shipments. In the nine years from 2004 through 2013, Kaspersky Lab detected 10 million malicious mobile installation packages. In 2014 alone, the number was 2.5 million installations, and it grew to 8.5 million in 2016
, according to the firm’s
Mobile Malware Evolution 2016 report.
Also in 2016, Kaspersky Lab detected 128,886 mobile banking Trojans and 261,214 mobile ransomware Trojans. The firm noted the following mobile security trends in 2016:
- Growth in the popularity of malicious programs using super-user rights, primarily advertising Trojans
- The distribution of malware via Google Play and advertising services
- The emergence of new ways to bypass Android protection mechanisms
- Growth in the volume of mobile ransomware
- Active development of mobile banking Trojans
In one example of a mobile malware exploit, an app portraying itself as a guide for
Pokémon Go was really a Trojan—and it was downloaded more than half a million times.
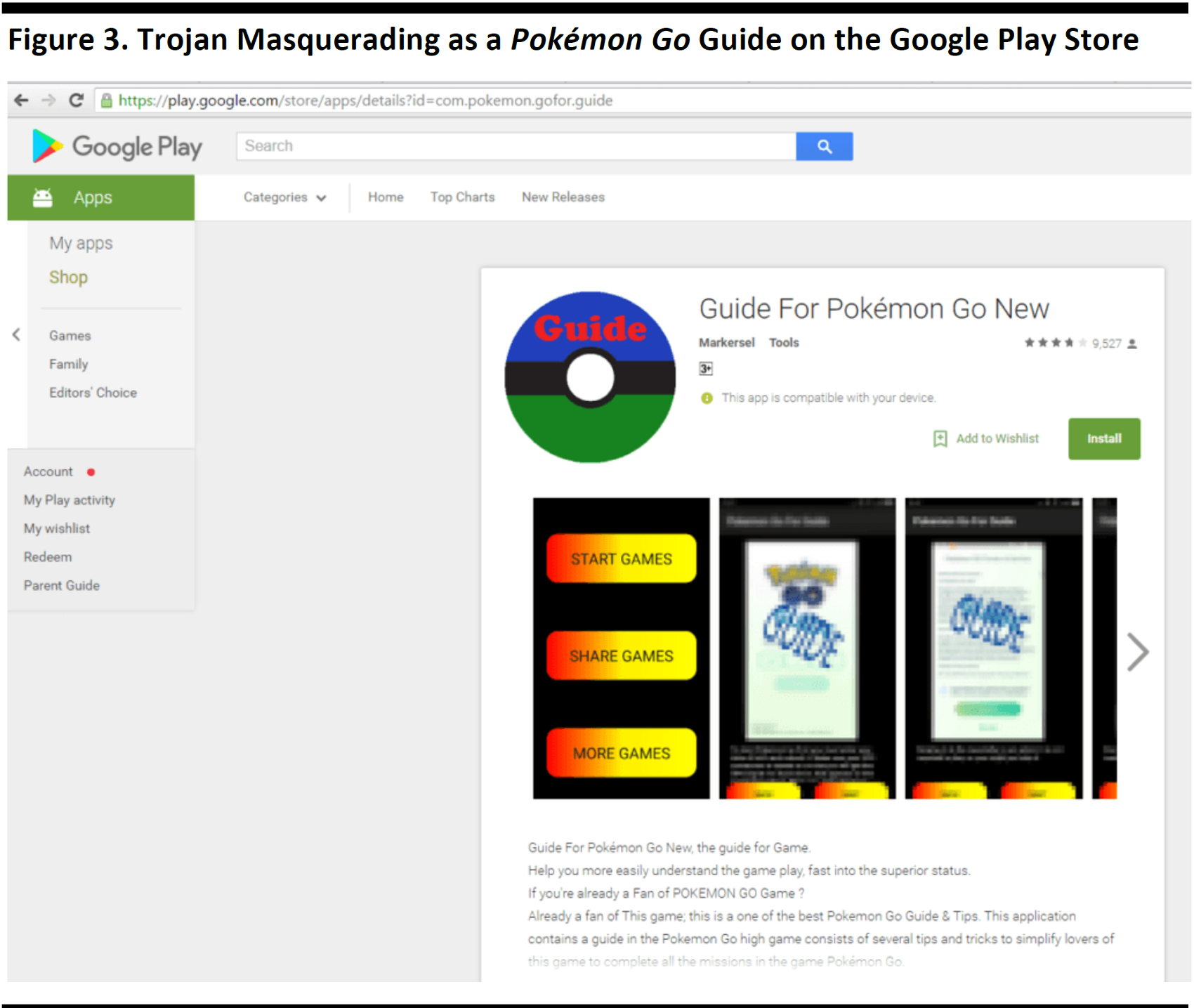
Source: Securelist.com
External Storage Devices/USB Drives
Everyday USB drives can also be vectors for malware. Although Mac PCs no longer automatically run programs found on a USB drive, a malware demonstration called BadUSB showed how a USB drive can be used to hack a PC. The instructions were released publicly, so that device manufacturers and PC users would be aware of the risks associated with the drives.
According to an October 2014 article in
PCWorld, in a BadUSB attack, a USB thumb drive connected to a computer automatically switches its profile to that of a keyboard and sends keystrokes to download and install malware and/or emulate the profile of a network controller to hijack domain name server settings on the PC.
Two experiments demonstrated that a large percentage of people are willing to insert drives with unknown provenance into their PC’s USB port:
- A group of paid testers dropped 20 USB sticks around the parking lot of a credit union, and 15 of the credit union employees plugged one into a computer, which then ran a program that connected with a test server.
- Another group of researchers dropped nearly 300 USB drives at six university campus locations, and at least 45% of the drives were eventually plugged into a computer, although some were scanned by the computers’ antivirus software.
In response, companies have developed isolation devices (USB “condoms”) such as SyncStop, which prevent data from passing into the host PC; they only enable recharging.
Public Wi-Fi Networks
Wi-Fi hotspots offer convenience and other benefits for users, as they require no authentication in order to use them. However, hackers can stealthily position themselves between users and the connection point, creating a hotspot with the same name in an attempt to fool users.PCs typically connect to the hotspot of a given name with the highest transmission power, and users can inadvertently connect to the hacker, rather than to the Internet. In the graphic below, “Tyrell Corporation” represents a hacker-created network.
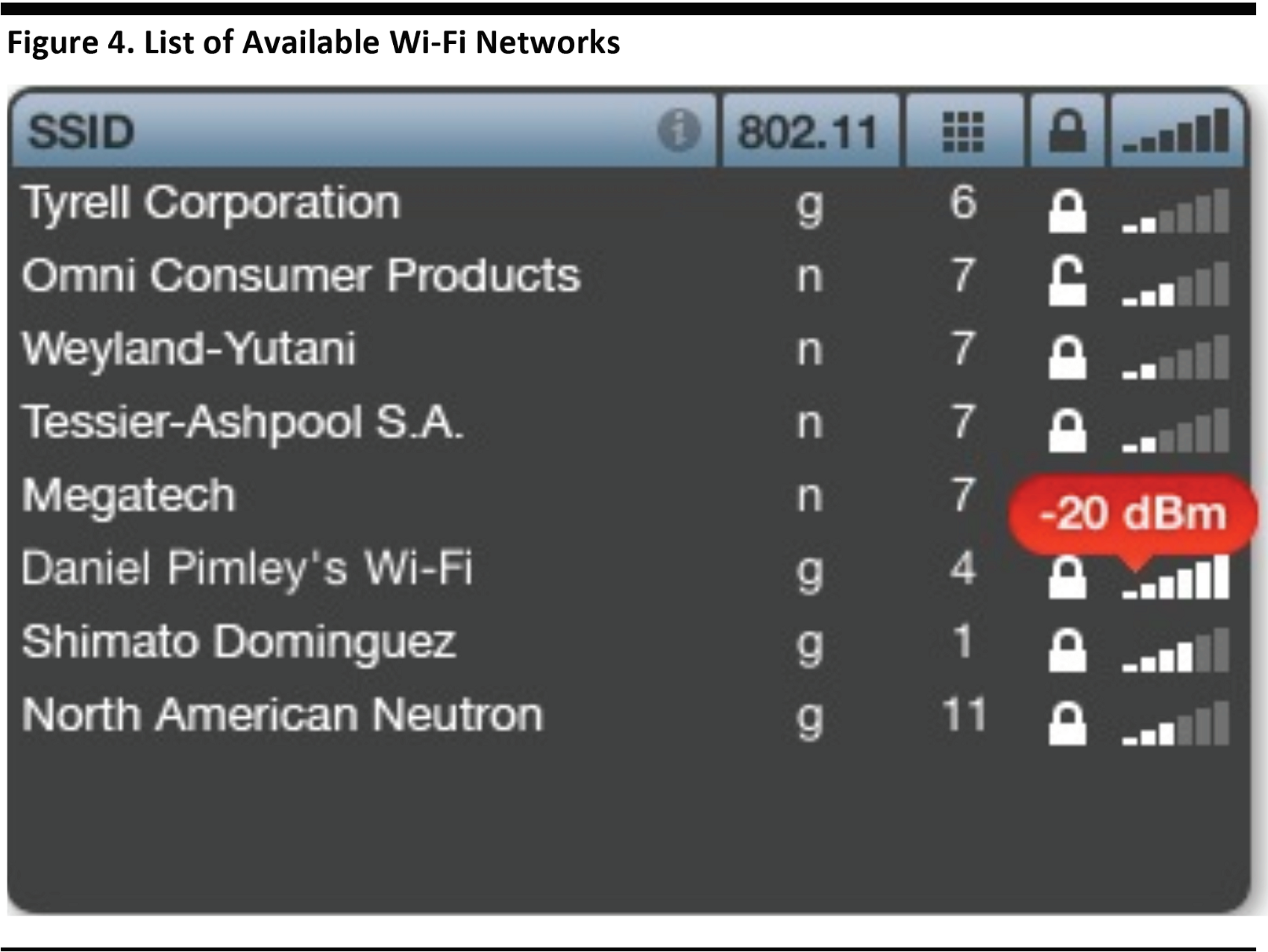
Source: Apple
Hackers can also distribute malware via unsecured Wi-Fi networks, if the Wi-Fi user has enabled file sharing. In some cases, connection points have been hacked, making the connection window appear to offer a software upgrade, which, if clicked on, actually installs malware.
Kaspersky Lab recommends taking the following actions to increase the level of safety in public Wi-Fi networks:
- Using a VPN
- Using SSL connections (URLs that begin with https://)
- Turning off file sharing
- Installing robust Internet security software on PCs
Security in the Cloud
On the surface, storing company data in the cloud—on a distributed group of servers across several locations—instead of on a server bearing a company’s name and URL seems like a good idea. Rather than purchasing computer hardware and hiring an expensive IT staff (information security analysts were paid a median salary of more than$90,000 per year in 2015, according to the US Bureau of Labor Statistics), using the cloud seems compellingly economical, representing a “pay as you go” use of computing resources. Moreover, a concentrated computing facility is likely to employ experienced professionals whose sole focus is on the facility’s performance and security. However, the aggregation of many companies’ sensitive business information at one or several unknown locations presents unique security risks: one server farm could represent a juicy target for hackers, offering access to the valuable data of several enterprises.
Cybersecurity Markets
IDC forecasts that global spending on cybersecurity will increase at an 8.3% CAGR between 2016 and 2020, growing from $73.6 billion to $101.6 billion. This growth rate is more than double the 3.3% CAGR that IDC forecasts for worldwide IT product revenue from 2015 through 2020. Other experts believe that the 2020 cybersecurity-spending figure could be as high as $200 billion, including the classified budgets for cyberdefense of the G-20 countries.
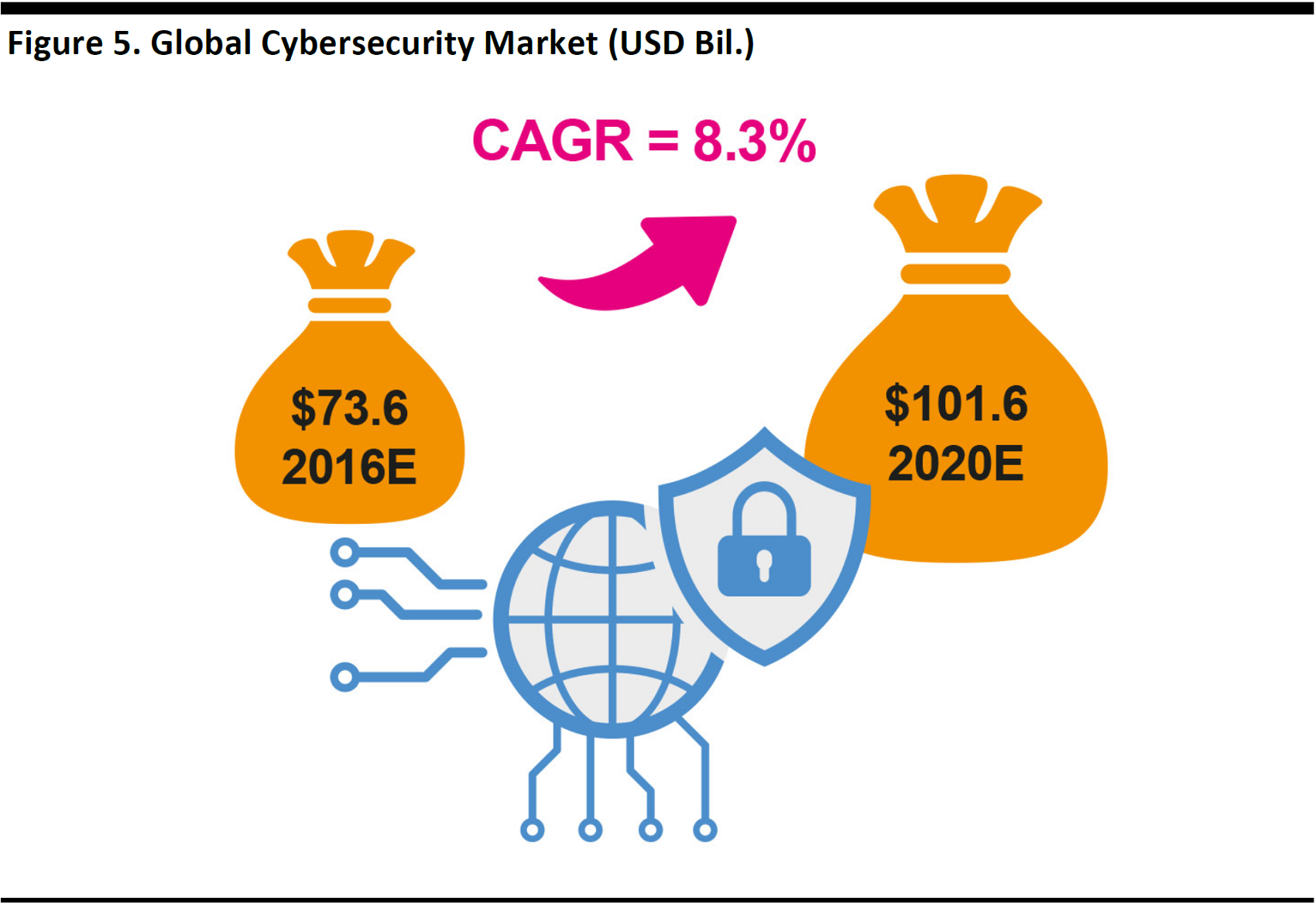
Estimates as of October 2016
Source: IDC
The largest category of cybersecurity spending is expected to be security services, representing an estimated 45% of 2016 global cybersecurity revenue, according to IDC. Security software is forecast to be the second-largest category, and user behavior analytics software is one of the fastest-growing market segments.
The US is the largest worldwide market for cybersecurity, also according to IDC, with industry spending in the country totaling $31.5 billion in 2016. Western Europe was in second place last year, at $19.5 billion.
Selected Cybersecurity Companies
A large number of companies are engaged in the business of cybersecurity. The Bessemer Venture Partners Cyber Index contains 29 public companies that are principally engaged in cybersecurity; of these, 16 have market values of at least $1 billion. Research firm Cybersecurity Ventures maintains a list of 500 leading global cybersecurity companies, based on several criteria, including customers, funding, growth, and marketing and branding.
Forbes extracted the top 10 companies in the Bessemer Venture Partners list, which are described in the table below.
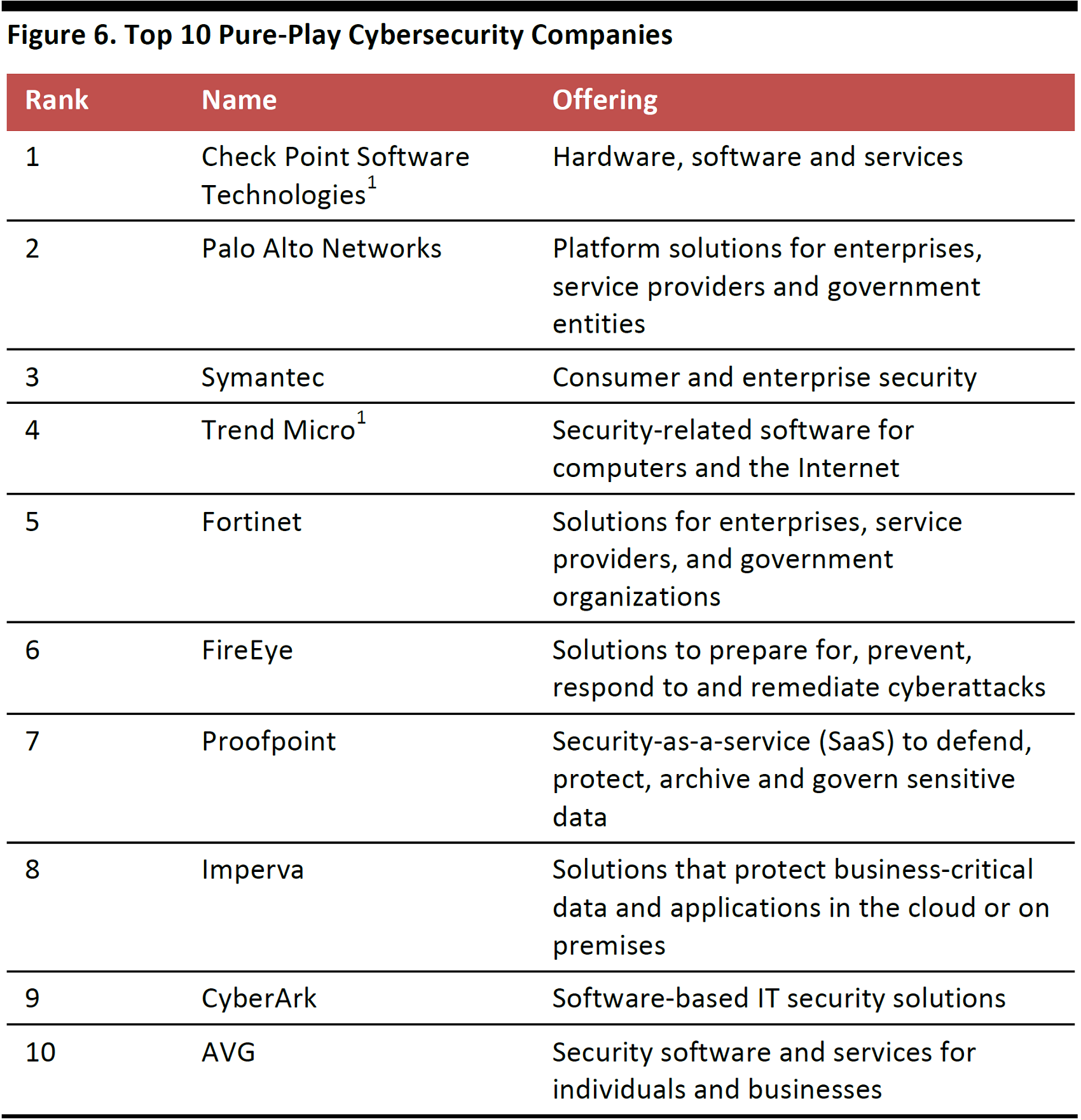
Source: Forbes
Other major names engaged in cybersecurity include networking equipment firms Cisco and Hewlett Packard Enterprise, RSA (a subsidiary of Dell), and Intel Security-McAfee (owned by Intel and private equity firm TPG).
There are also a large number of startups engaged in cybersecurity, fueled by healthy financing levels in 2015 and 2016. The graph below shows the number of cybersecurity financing deals over the past several years as well as total deal value in each of those years.
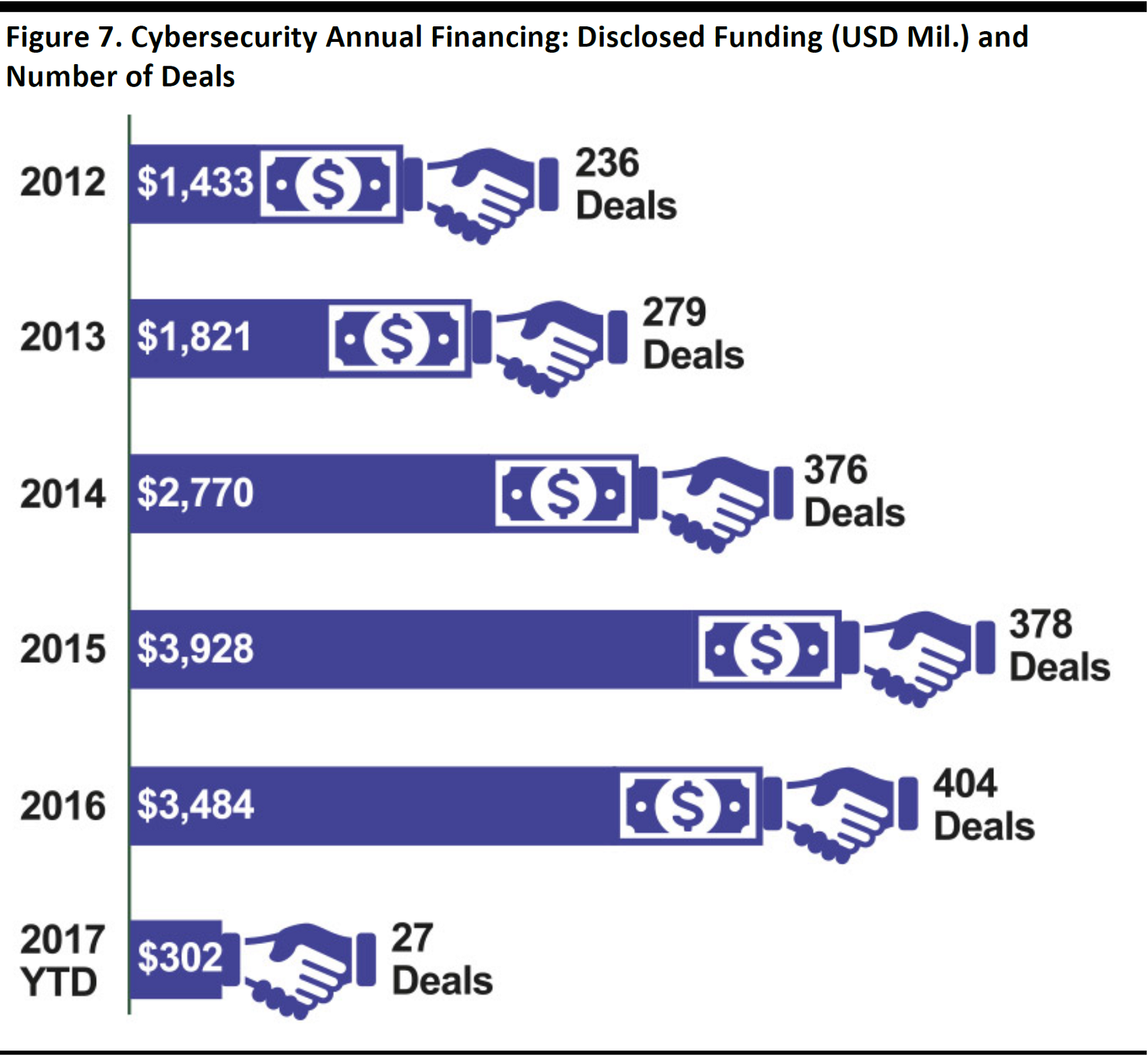
As of February 7, 2017
Source: CB Insights
Conclusion
Thieves and vandals have been taking advantage of their fellow humans since the beginning of time, and the dawning of the Information Age has drawn contemporary miscreants’ attention to PCs and servers. The advent of the Internet has shortened the distance between foreign hackers and our computing devices. The Internet has also become a darker place due to the activities of organized criminal gangs and state-sponsored hacking groups. Cybercriminals are relentless and tireless, and we have to overcome our own tendencies toward apathy and carelessness in order to thwart them. Fortunately, there are good actors and an entire, growing industry of companies that are using their substantial expertise to deliver cybersecurity solutions designed to protect us.


 Forecasts as of March 2017
Source: IDC
Forecasts as of March 2017
Source: IDC



