Executive Summary
Ever since humans began treasuring objects of value, there have been individuals who have wanted to steal or damage those objects. In our current era, the Information Age, data represent many of our objects of value. PC viruses have existed essentially since the advent of the PC. And as the PC’s capabilities have increased over time, following Moore’s law, so, too, has the value of the data residing on them, making them an attractive target for criminals.
The invention of the Internet has made the world flat, enabling us to shop and make purchases from faraway countries. At the same time, it has enabled invisible criminals at home and abroad to sometimes break into our PCs and take our data, lock up our devices in exchange for ransom, or cause other types of havoc.
At one time, cybersecurity simply consisted of protecting computers from viruses and malware that could be hidden on a floppy disk. Now, computer users are vulnerable to picking up such maladies while browsing the web, using a mobile phone, logging into a free Wi-Fi service or even plugging in a USB stick they might have found.
Unfortunately, the Internet has become a darker place. In the past, teenage hackers might have broken into computer systems in order to demonstrate their abilities and cause minor chaos, but now, organized criminal gangs are colluding with state-sponsored hacking groups to engage in larceny, extortion, and corporate and private espionage. Moreover, some miscreants are now invading computers and encrypting the hard drive, threatening to release it only in exchange for a hefty ransom payment made in untraceable bitcoin.
For both individuals and enterprises, it is a struggle to keep the bad actors at bay. They are relentless and tireless, and all it takes is one person clicking on the wrong email link to let them in. Cyberattacks are largely enabled by the human element—by our own apathy, inattention to detail or lack of vigilance. Hackers often get in when IT managers do not apply software updates or patches or do not heed the yellow and red flags generated by security monitors. And many IT teams do not have a plan in place to deal with break-ins, which are almost inevitable. The burden of cybersecurity falls on all of us: to keep cybercriminals out, we must stay on top of our game and not doze off.
Enter the good guys, offering cybersecurity solutions. Just as we have to buy locks to protect our homes, IT managers have to arm themselves with a suite of tools to fend off network invasions, or at least minimize their effects. The negative PR and business consequences that can result from a network incursion are just too great a risk to not deal with the cybersecurity threat proactively, as many retailers and government agencies have painfully learned.
In this report, we provide a general overview of cybersecurity, the different types, and methods of cyberattacks, and many details about the industry and the companies that are working to keep our devices and networks safe from cybercriminals.
About This Deep Dive
Fung Global Retail & Technology is publishing its
Deep Dive: An Introduction to Cybersecurity in three installments.
The Executive Summary outlines the growth of the Information Age and the advent of the Internet, the benefits of which have been tested often by corresponding developments in computer viruses and malware. Recently, though, the Internet has become a significantly darker place. The bad actors online used to be mostly teenage hackers, but they are being replaced by organized crime syndicates and state-sponsored hackers with much bigger criminal ambitions. The good guys have labored to keep pace with the cybercriminals, and a rich cybersecurity industry has emerged, with a large number of companies specializing in the various aspects of online security.
Part One: Introduction and Components of Cybersecurity
The growing interconnectedness of computers and increased use of the Internet make computers an irresistible target for cybercriminals. As Internet usage has increased and hacking tools have become more accessible, the number of reported cyberattacks has risen. The cat-and-mouse game between virus developers and antivirus software makers continued relatively peacefully until about 2010, when the balance between hackers and defenders was severely altered.
In 2013, the National Institute of Standards and Technology defined five categories in a framework for reducing cyber-risks to infrastructure: identification, protection, detection, response, and recovery.
Part Two: Components of an Advanced Attack, Characteristics of an Advanced Persistent Threat, and Types of Attacks and Hackers
The term “APT” refers to an advanced persistent threat, a cyberattack in which an unauthorized person gains and maintains access to a network for an extended period of time. Recent APTs have targeted enterprises.
APTs can take a number of forms, including malware, spam, botnet and ransomware attacks, and hackers can take advantage of vulnerabilities in systems, such as the use of weak or common passwords.
Types of hackers include script kiddies and white, black, gray, green, red and blue hats.
Part Three: New Threats/Threat Vectors, Markets, and Cybersecurity Companies
The number and kinds of cyber threats continue to grow and evolve due to advances in technology that benefit both attackers and defenders.
Market intelligence firm IDC forecasts that global spending on cybersecurity will increase at an 8.3% CAGR between 2016 and 2020, growing from $73.6 billion to $101.6 billion. This growth rate is more than double the 3.3% CAGR that IDC forecasts for worldwide IT product revenue from 2015 through 2020.
The Fung Global Retail & Technology team hopes that you will find this
Deep Dive interesting and informative and that it will help you protect your enterprise against cybersecurity threats!
Key Takeaways
- First of all, companies need a cybersecurity plan that provides information and resources and outlines responsibilities in the event of a (likely) cyberattack.
- Enterprises must take a holistic view of cybersecurity, including identification, detection, response and recovery.
- Network hygiene is essential; companies need to keep all software (including enterprise resource–planning software) patched and updated, and they must stay abreast of developments in cybersecurity.
- Enterprises need to heed alerts and warnings, and they likely need a solution that distinguishes between critical and noncritical alerts.
- There are many companies, including many startups, that are developing solutions using artificial intelligence (AI), although AI should be but one tool in the arsenal.
- There are many endpoints, i.e., routes and devices through which malware can enter a network, including web pages, mobile devices, IoT-connected devices, point-of-sale systems, vendor interfaces and wireless networks. All of these must be considered when creating or updating a cybersecurity plan.
- Moving data to the cloud solves many security issues, but it means that the security of the data center becomes paramount.
According to global IT company Cisco, organizations must integrate their security technology, simplify their security operations and rely more on automation.
Source: cisco.com
Introduction
The growing interconnectedness of computers and increasing use of the Internet make computers an irresistible target for cybercriminals. Cisco forecasts that Internet traffic will grow at a 47% CAGR from 2016 through 2021.
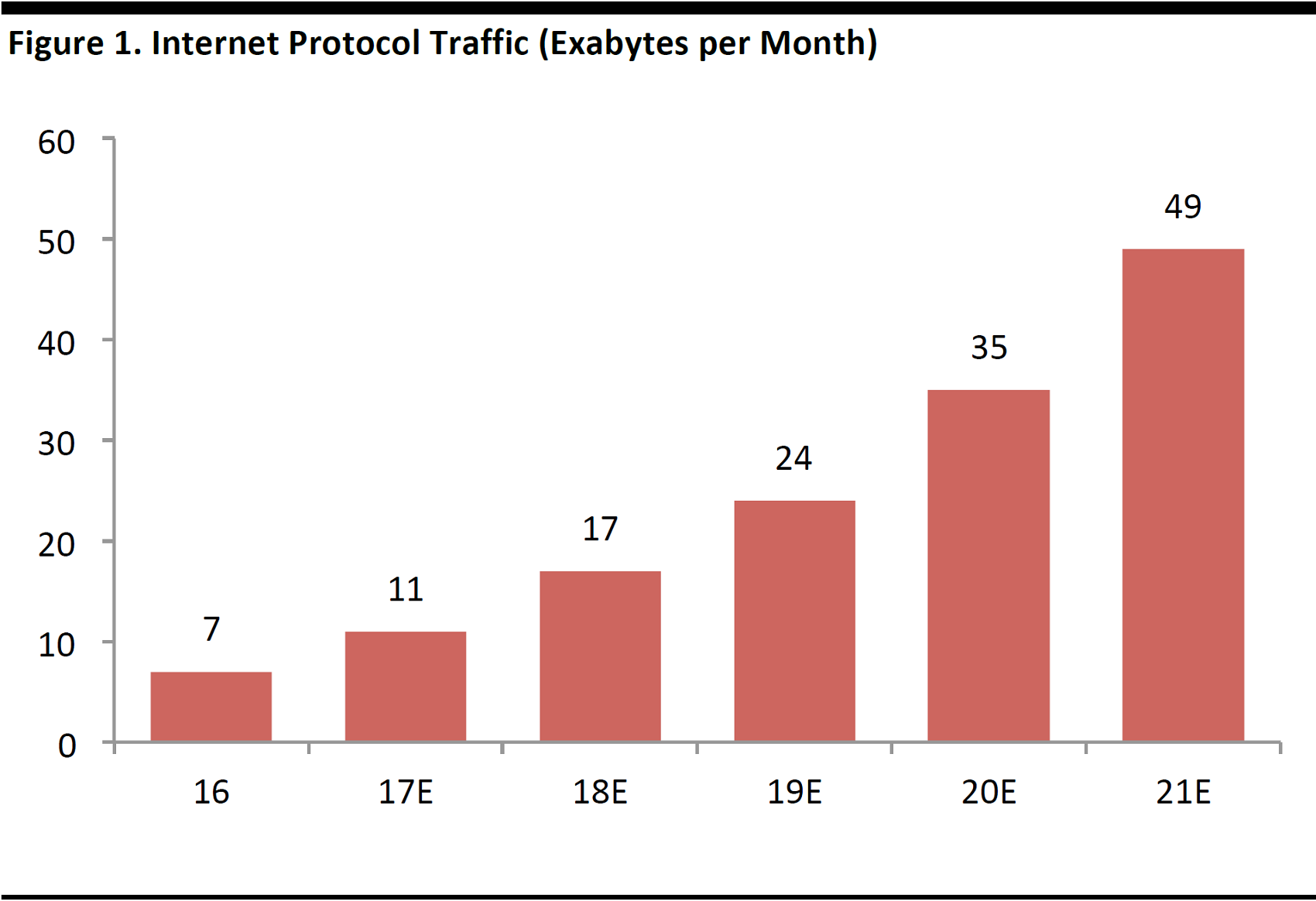
One exabyte is one quintillion (1018) bytes, or one billion gigabytes.
Source: Cisco,Visual Networking Index:Global Mobile Data Traffic Forecast Update(2017)
The history of computer viruses generally parallels the development of the PC industry. Some self-replicating computer programs were demonstrated on ARPANET (the predecessor of today’s Internet) in the early 1970s, but the Elk Cloner virus was the first real virus to appear “in the wild,” showing up on the Apple II in 1982. The Brain virus appeared on IBM PCs in 1986.
The cat-and-mouse game between virus developers and antivirus software makers continued relatively peacefully until around 2010, when the balance between hackers and defenders was severely altered. That year, the hacking tools of nation-states became available on the dark web for about $300 (or the equivalent in untraceable bitcoin), according to cybersecurity experts. The availability and affordability of these sophisticated tools understandably resulted in a spike in the number of sophisticated attacks on enterprises and government agencies.
As Internet usage has increased and hacking tools have become more accessible, the number of reported cyberattacks has risen. The graph below shows a steady increase in the number of information-security incidents reported to US federal agencies (the reporting methodology changed in 2016, as noted).
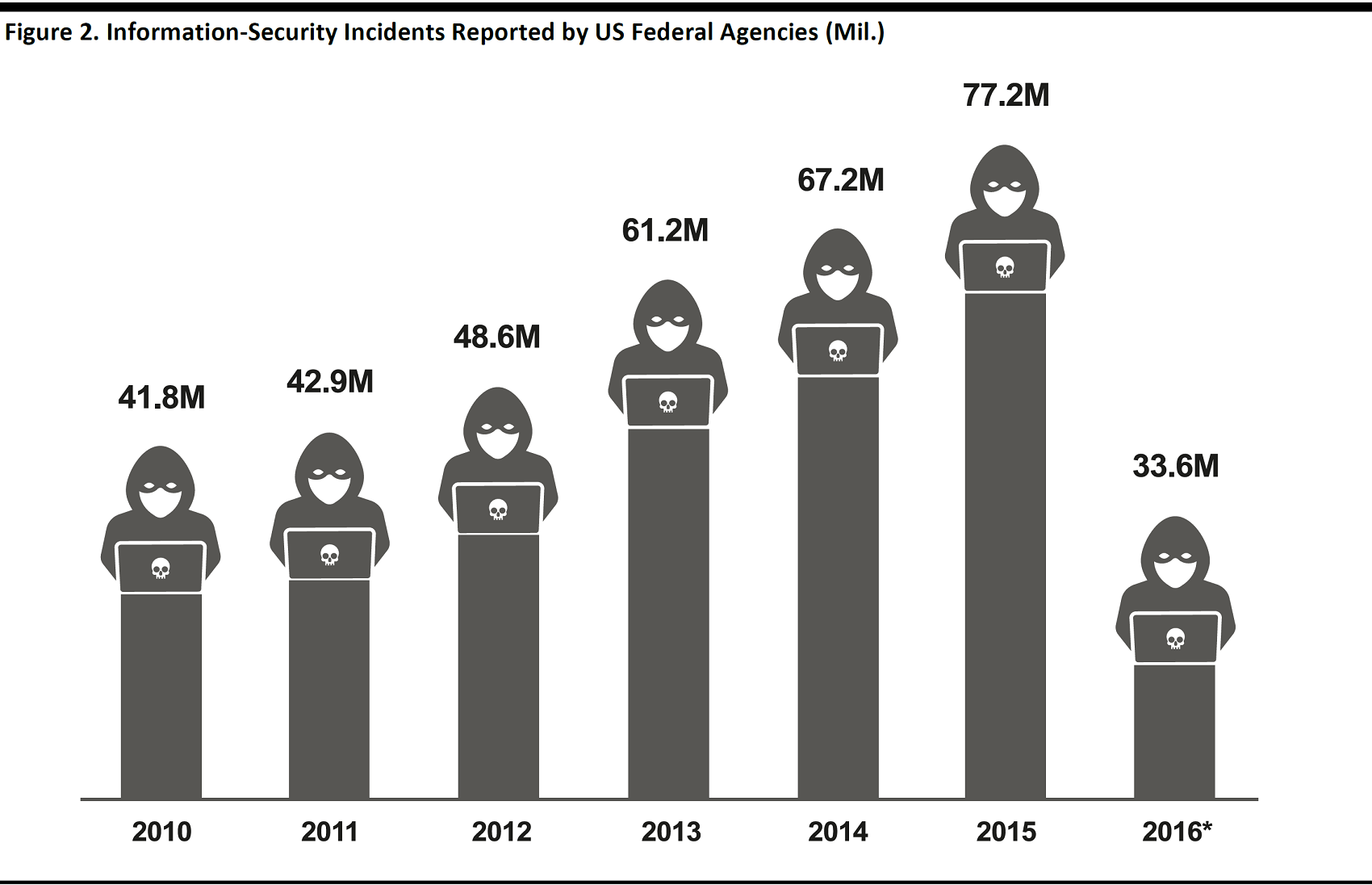
*Incident reporting requirements were revised in 2016 and agencies are no longer required to report non-cyber incidents or attempted scans or probes of agency networks.
Source: US Government Accountability Office/US Office of Management and Budget
Cybersecurity software firm Kaspersky Lab has published several key statistics on the cybersecurity environment in 2016:
- Over the year,31.9% of users’ computers in the Kaspersky Security Network who agreed to provide data were subject to at least one malware-class web attack.
- Kaspersky Lab’s solutions repelled 758,044,650 attacks launched from online resources located all over the world.
- Web antivirus components recognized 261,774,932 unique URLs as malicious.
- Kaspersky Lab’s web antivirus software detected 69,277,289 unique malicious objects.
- Of unique Kaspersky Security Network users’ computers,1,445,434 were targeted by encryptors.
- Kaspersky Lab’s solutions blocked attempts to launch malware capable of stealing money via online banking systems on 2,871,965 devices.
Furthermore, the company notes that half of cyberattacks in 2016 were made through web browsers.
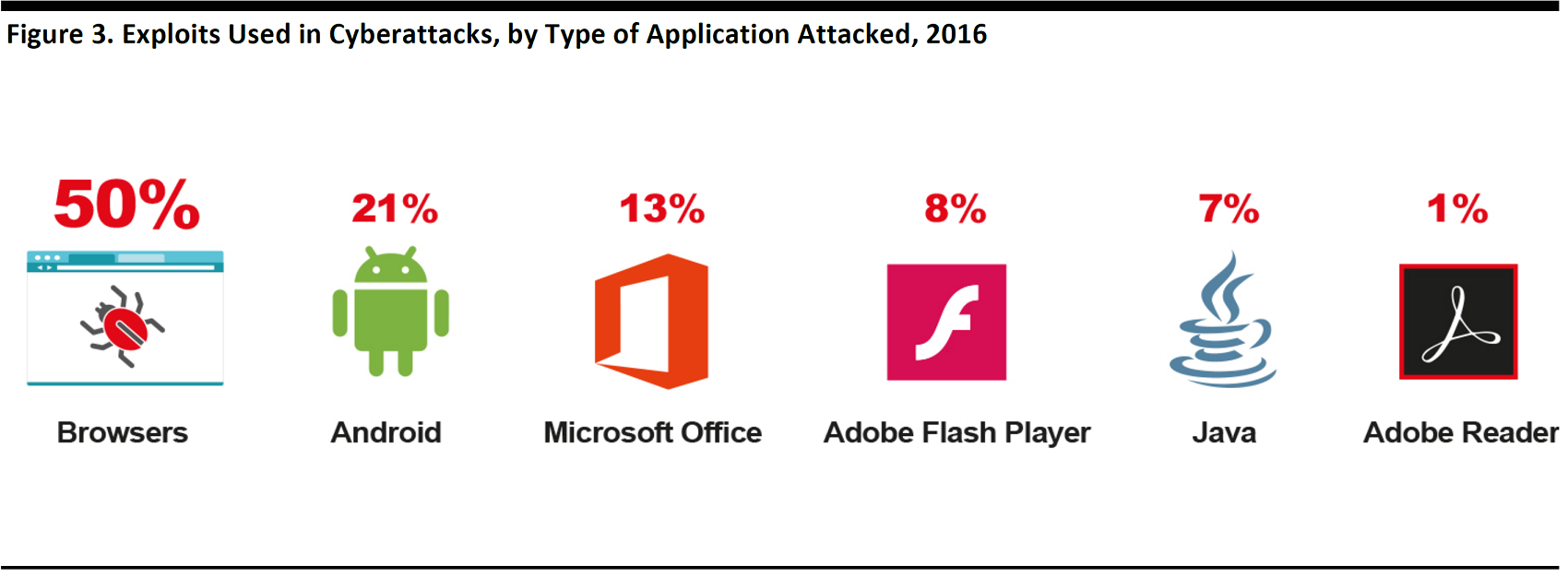
Source: Kaspersky Lab, Kaspersky Security Bulletin 2016
The graphic below shows the results of a Cisco survey of security professionals regarding their greatest sources of concern.
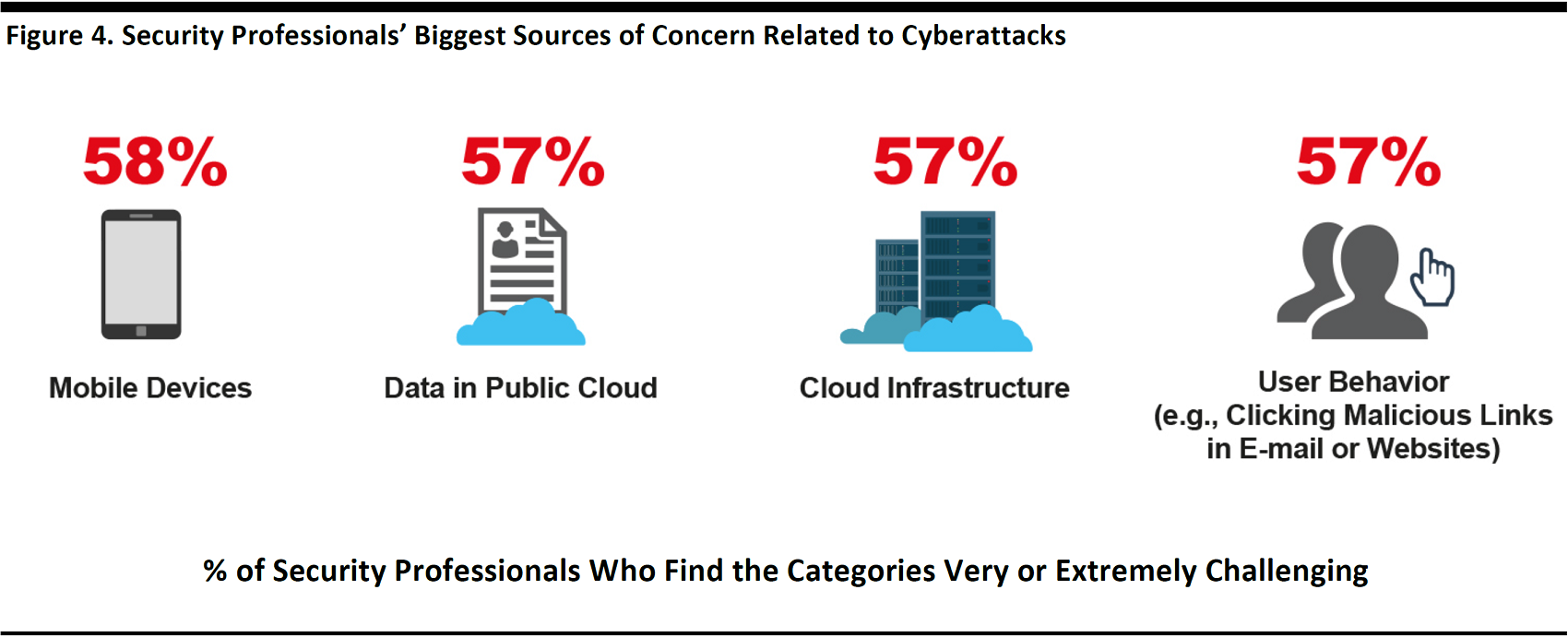
Source: Cisco, Visual Networking Index: Global Mobile Data Traffic Forecast Update (2017)
Adversaries are using a vast and varied portfolio of techniques to gain access to organizational resources and attain unconstrained time in which to operate. Cisco has distilled these techniques into three main types:
- Taking advantage of lapses in patching and updating
- Luring users into socially engineered traps (“spearphishing”)
- Injecting malware into supposedly legitimate online content such as advertising
Other means of gaining access to networks or PCs include exploiting middleware vulnerabilities and inserting malicious spam.
Components of Cybersecurity
Following the issuance of an Executive Order in 2013, the National Institute of Standards and Technology defined five categories in a framework for reducing cyber-risks to infrastructure: identification, protection, detection, response, and recovery.
Source: nist.gov
1. Identification
Enterprises need to first undertake an accounting of the systems, assets and data they seek to protect, including an inventory of physical devices within the organization. In this stage, organizations need to codify their security policy and define the responsibilities of individuals within the organization. The policy also needs to be distributed to all employees to ensure awareness.
2. Protection
Protection includes domain name server monitoring of visits to undesired websites. Many approaches require endpoint devices such as PCs, laptops, smartphones, tablets and other peripherals to meet specific criteria before they can access network resources. Other examples of protection measures include:
- Firewalls, which control applications
- Controlling network traffic
- Lockdown
- Passwords
- “Air gapped” PCs (which are not connected directly to the Internet or to any other computers that are connected to the Internet), or PCs connected through a DMZ (demilitarized zone) that provides an additional layer of security between PCs and the outside world
- AI
3. Detection
There are several software packages available that aim to protect networks, including virus blockers and file scanners that detect various types of malware. Detection also includes monitoring the use of system resources, the use of administrator or privileged functions, and unauthorized access.
AI is used across many product categories. It can be used to compare incoming attachments or URLs with typical cases, in order to learn which ones are out of the ordinary. It can also be used to sort through the large number of security warnings that many systems generate, in order to determine which ones appear to be urgent and require immediate human intervention. The graphic below illustrates how such warnings might be analyzed to determine the level of threat they represent.
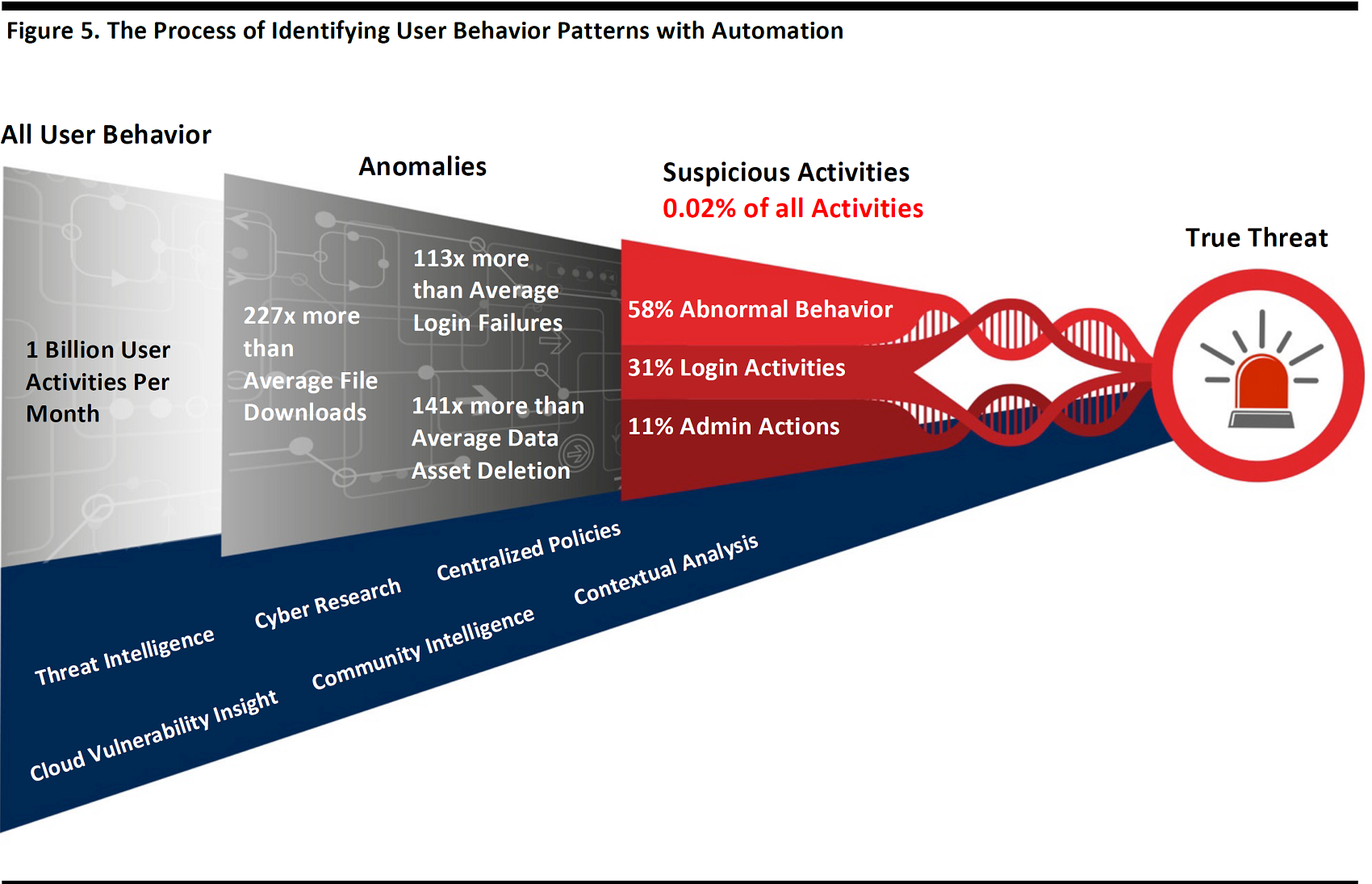
Source: Cisco, 2017 Annual Cybersecurity Report
4. Response
There are products available that assist IT managers in locating an incursion and terminating it by canceling access to resources such as directories, data, passwords and communication pathways. Well-prepared companies have plans in place to deal with an incursion, and have determined which individuals are responsible for which areas.
5. Recovery
Finally, there are tools that help companies restore their systems to the pre-attack state by repairing any damage and restoring any deleted data. These tools are designed to patch vulnerabilities and help companies benefit from the experience, so as to shorten the recovery time after the next attack.







