
DIpil Das
What’s the Story?
Despite the advent of advanced cybersecurity tools, major security breaches continue. Hackers are now attacking data stored in the cloud as well as providers of Internet and cybersecurity tools. Retailers are a particularly attractive target for hackers as they possess customer and payment data, and point-of-sale (POS) terminals represent another connected device that can be attacked. The recent move of many employees accessing corporate networks from home creates opportunities for weaknesses in home networks and hardware to turn into security breaches. In this report, we discuss recent developments in the cybersecurity space and provide an overview of the types of hacking and strategies for defense.Why It Matters
The total global cost of cybercrime and spending on cybersecurity exceeded $1 trillion in 2020, according to a report published by McAfee and the Center for Strategic and International Studies. The combination of high rewards, low risk and the decentralized structure, low cost and anonymity of the Internet present low entry barriers for many types of cybercriminals. Retailers need to do everything within their power to keep customer and payment data secure to protect their reputations so that consumers feel safe shopping with them. This has become even more urgent since the outbreak of Covid-19 as e-commerce penetration has stepped up to a higher level and many workers are accessing corporate networks from home. Retailers have historically been victim to several notable data breaches and want to do everything possible to prevent damage to their reputations.Cybersecurity and Retail: In Detail
During 2020, there was an increase of IT supply chain-related security breaches, which is a huge concern for retailers—and the migration to cloud computing creates additional risk. Several leading technology companies and innovators offer cybersecurity solutions, and growing venture funding indicates that many future leaders are set to emerge in the market. How Can Retailers and Other Enterprises Boost Cybersecurity? The simplest, most effective cybersecurity defenses largely remain network hygiene—i.e., keeping software up to date—and confining users’ access within appropriate sections of the network. Given the dramatic increase in phishing attacks, training employees to increase their skepticism of correct-seeming e-mails can also reduce the number of threats to the network. Many incursions are the result of human error or negligence, by not keeping software and patches up to date to address known vulnerabilities. Cloud computing offers a likely solution to this, as the software is updated frequently and automatically during the year, so clients will always have the latest version. Since many breaches result from an intruder gaining full access to, and privileges within, a network, measures to control and limit access are compelling. For example, the concept of the principle of least privilege (where every module only accesses the resources necessary for its purpose), makes sense. There are several technologies that help confirm a user’s identity on the network:- USB drives or dongles that contain security tokens that physically confirm the users’ identity. Google virtually eliminated phishing attacks since 2017 following the deployment of physical security keys.
- Zero-trust networks do not assume that networked devices such as laptops should be trusted by default; rather, they use mutual authentication to test the integrity of these devices, even if they are connected inside the company’s own network.
- Artificial intelligence (AI)-based solutions that monitor a user’s behavior in the network and compare this behavior to a baseline.
Figure 1. Number of US Data Breaches and Exposures (Left Axis) and Individuals Affected (Mil.; Right Axis) [caption id="attachment_126767" align="aligncenter" width="725"]
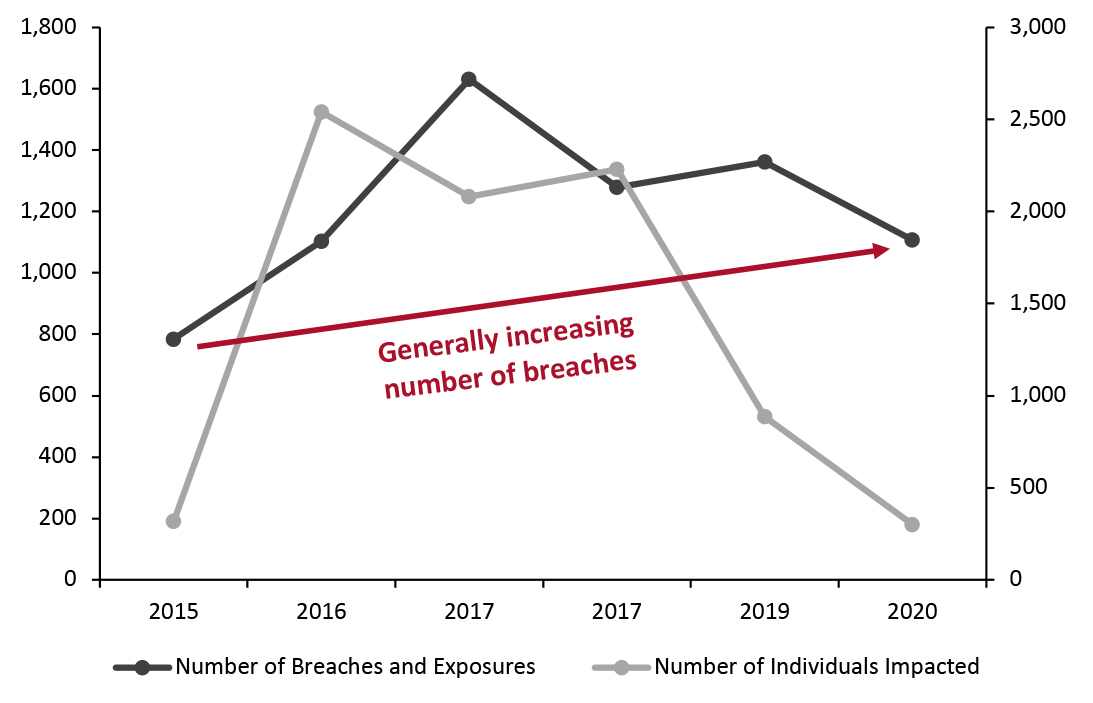 Source: Identity Theft Resource Center 2021[/caption]
Looking at the root causes of compromises in 2020, e-mail/phishing was the number-one cause, followed by remote-access attacks. The dominance of this category reflects hackers’ success in gaining entry to networks through targeted individuals, rather than other means.
Source: Identity Theft Resource Center 2021[/caption]
Looking at the root causes of compromises in 2020, e-mail/phishing was the number-one cause, followed by remote-access attacks. The dominance of this category reflects hackers’ success in gaining entry to networks through targeted individuals, rather than other means.
Figure 2. Percentage of Claims by Attack Technique [caption id="attachment_126768" align="aligncenter" width="725"]
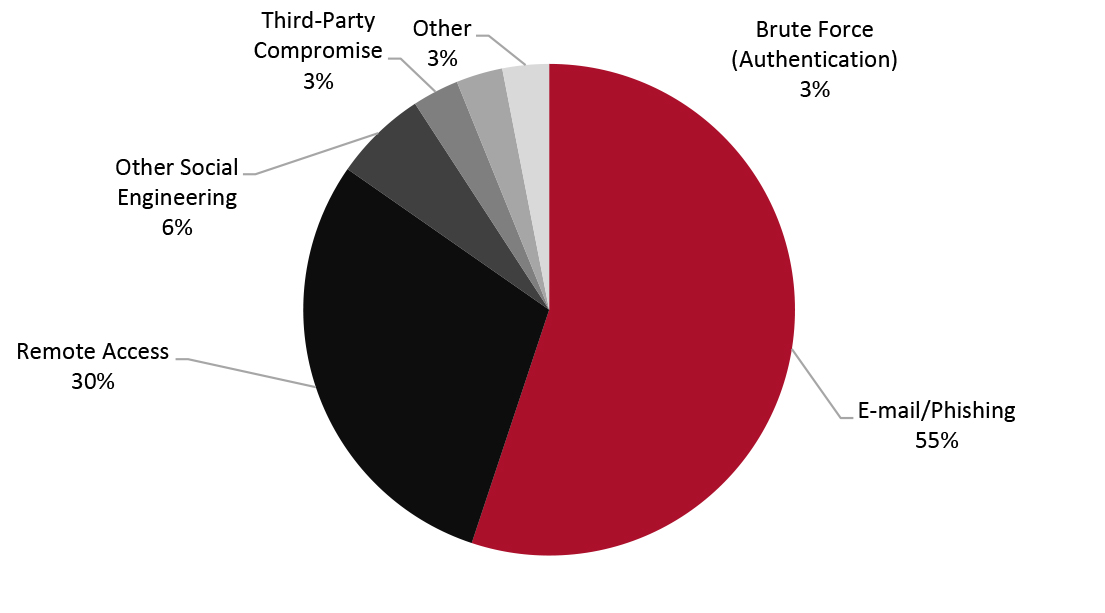 Source: helpnetsecurity.com[/caption]
Particularly troubling for retailers (and consumers) is that the number of attacks on the technology supply chain (i.e., on technology providers) increased sharply during the first nine months of 2020, as consumers sheltered at home and purchased more goods online. The number of attacks in the end of 2020 likely result from technology providers reviewing and tightening up their own cybersecurity defenses.
Source: helpnetsecurity.com[/caption]
Particularly troubling for retailers (and consumers) is that the number of attacks on the technology supply chain (i.e., on technology providers) increased sharply during the first nine months of 2020, as consumers sheltered at home and purchased more goods online. The number of attacks in the end of 2020 likely result from technology providers reviewing and tightening up their own cybersecurity defenses.
Figure 3. Number of Individuals or Systems Affected by Third-Party/Supply Chain Compromises, 2020 [caption id="attachment_126769" align="aligncenter" width="725"]
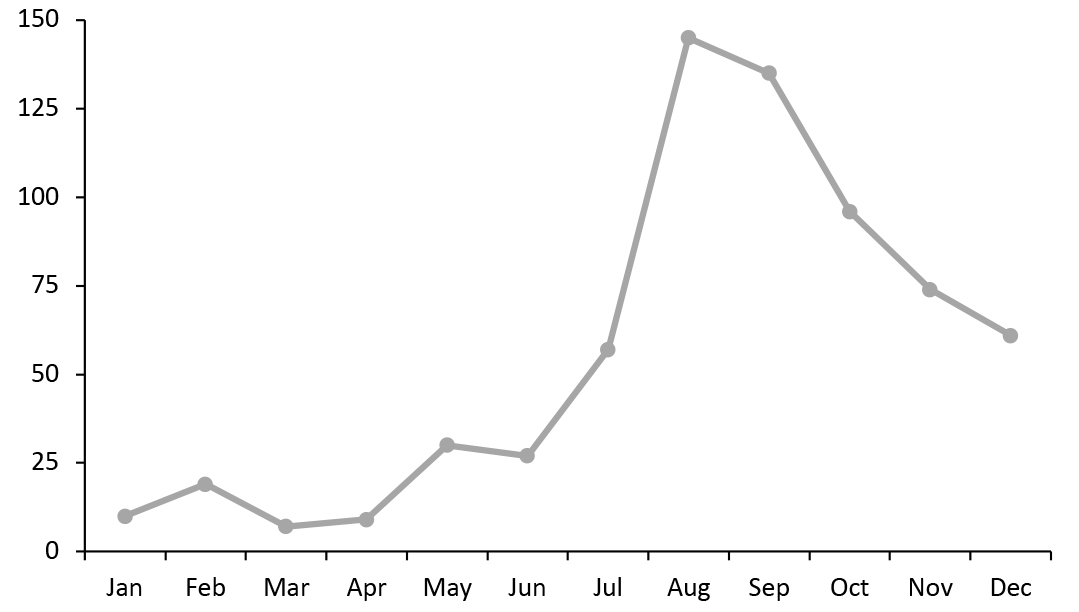 Source: Identity Theft Resource Center 2021[/caption]
Quantum computing could present a new, serious risk to retailers and consumers. Quantum computers perform certain types of calculations at orders of magnitude of higher speed, possibly able to break a 2,084-bit RSA encryption code within eight hours, based on work performed by Google and the KTH Royal Institute of Technology in Sweden. Future commerce could require quantum computing-fueled encryption and decryption engines.
Cyberattacks
The number and types of cyberattacks continue to evolve, as technology and computing power advance alongside the growing migration to cloud computing and the large number of employees accessing their corporate networks while working from home.
Types of cyberattacks and vulnerabilities include the following:
Source: Identity Theft Resource Center 2021[/caption]
Quantum computing could present a new, serious risk to retailers and consumers. Quantum computers perform certain types of calculations at orders of magnitude of higher speed, possibly able to break a 2,084-bit RSA encryption code within eight hours, based on work performed by Google and the KTH Royal Institute of Technology in Sweden. Future commerce could require quantum computing-fueled encryption and decryption engines.
Cyberattacks
The number and types of cyberattacks continue to evolve, as technology and computing power advance alongside the growing migration to cloud computing and the large number of employees accessing their corporate networks while working from home.
Types of cyberattacks and vulnerabilities include the following:
- Malware—Including bots, Trojan horses, viruses and worms
- Spam—Unwanted and irrelevant e-mail
- Botnets—A large number of infected, controlled computers
- Distributed denial of service (DDoS)—A botnet attempting to overload a server with superfluous requests
- Ransomware—Malware that takes over a user’s computer in an attempt to extort payment
- Privilege escalation—Exploiting a bug or weakness to gain undeserved resources or access
- Exploits—Using a command, methodology or routine to take advantage of security vulnerabilities
- Backdoors—Secret, undocumented ways of accessing a system
- Bad passwords—Using words available in standard dictionaries, which are easily guessable
- Hacktivism/vigilantism/cyber-dissidents/cyber-shaming—Hacking to promote a political or social goal
- Infection—The attacker enters and gains control of the host
- Persistence—The malware remains within the network until activated
- Communication—The malware establishes a communication channel with the attacker
- Command and Control—The attack is controlled, managed and updated over time.
- In late 2020, a security lapse by Prestige Software, provider of hotel management and reservation software, led to the exposure of more than 10 million files containing data from travel providers Booking.com, Expedia and Hotels.com.
- In mid-2019, a cloud misconfiguration enabled a hacker to access data from Capital One regarding more than 100 million people in the US and Canada, which led to the arrest of a former Amazon Web Services engineer.
- Check Point—The company offers a consolidated cybersecurity solution across cloud, networks, endpoints, mobile and IoT, as well as a 24/7 incident response team.
- Cisco—Solutions include secure access service edge (SASE), cross-layered detection (XDR), and zero trust, based on the SecureX security platform.
- CrowdStrike—The Falcon platform leverages cloud-scale AI and offers real-time protection and visibility, preventing attacks on endpoints and workloads on or off the network.
- Fortinet—The company provides security fabric architecture for large enterprises, service providers and government organizations in the networked, application, cloud and mobile environments.
- IBM—Offerings include security platforms, data-security products, and identity- and access-management products and services.
- McAfee—Positioned as a device-to-cloud cybersecurity company, McAfee offers solutions for consumers and businesses.
- Microsoft—Security is built into the Azure cloud platform and the 365 suite of office apps.
- Palo Alto Networks—The company claims to be the global cybersecurity leader, offering technology for a cloud-centric future.
- RSA—RSA provides solutions to detect and respond to advanced attacks, manage user access and reduce operational risk, fraud and cybercrime.
- Trend Micro—The company offers solutions for businesses, governments and consumers across cloud workloads, endpoints, email, IIoT (industrial IoT) and networks.
- Cato Networks—The company’s SASE platform merges converging software-defined networking in a wide-area network, network security and zero-trust network access into a global, cloud-native service.
- Cybereason—The company’s platform combines detection and response, next-generation antivirus and proactive threat hunting for analysis of every element of a malicious operation.
- Darktrace—The company offers a self-learning AI-based technology that autonomously detects, investigates and responds to advanced cyber threats, including insider threat, remote working risks, ransomware, data loss and supply chain vulnerabilities.
- Illumio—Products operate on the principle of least privilege to provide visibility and segmentation for endpoints, data centers or clouds.
- OneTrust—OneTrust offers privacy, security and governance programs for compliance with GDPR and other global privacy and security laws.
- SentinelOne—The company focuses on endpoint security with a platform that combines behavioral-based detection, advanced mitigation and forensics in real time.
Figure 4. VC Cybersecurity Funding (USD Bil., Left Axis) and Number of Mega-Rounds (Right Axis) [caption id="attachment_126770" align="aligncenter" width="725"]
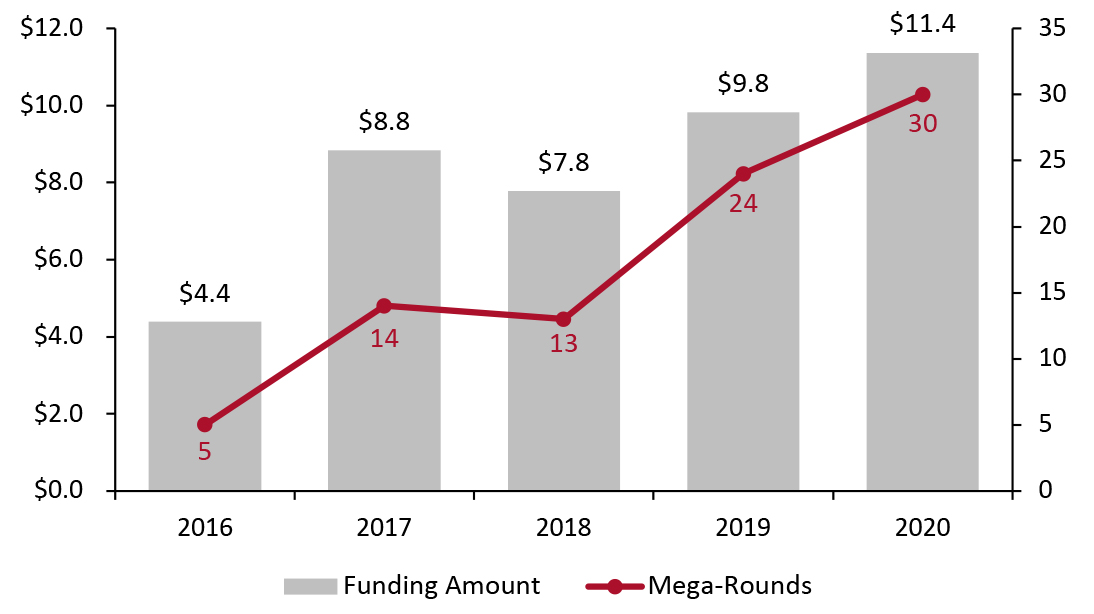 Source: CB Insights[/caption]
Source: CB Insights[/caption]
What We Think
Defending customer and payment data is becoming ever-more urgent, as bad actors continue to step up their game, most recently attacking the providers of software tools. Moreover, many of these actors represent state-sponsored or organized crime groups. Fortunately, there is an industry of innovators developing tools to thwart bad actors, fueled by technologies such as AI. Implications for Brands/Retailers- Brands and retailers need to stay current on the latest tools and techniques for protecting their networks and data.
- Technologies such as tokenization enable the encryption and storage of payment information in a secure location outside the retailer.
- The retailer’s reputation as a safe place to shop depends on maintaining data security.
- Real-estate firms have their own data on their tenants, which also needs to be protected.
- The estate firms also possess data on their retailer tenants, which also needs to be protected to maintain the retailers’ reputations.
- Technology vendors have received recent wakeup calls that their tools are now the target of security breaches and need to step up their defenses.
- There is a robust sector of innovators providing cybersecurity tools for enterprises.
- Technologies such as AI, which excel in finding unseen relationships among data, are strong in identifying behaviors and patterns that do not match historical data.
- Quantum computing is an emerging field that is likely to have massive implications for encryption and commerce.