EXECUTIVE SUMMARY
In the previous reports in this series, we examined the various segments of the connected-home market. We looked at different gadgets and the features that distinguish them as smart products. In this concluding report, we recap some of the smart home market drivers, explore the barriers to adoption and offer some thoughts on the future of the connected home.
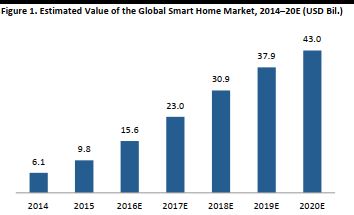
The global smart home market was valued at $9.8 billion in 2015, according to Statista, and it is estimated to reach $43.0 billion in 2020. Household Internet connectivity and smartphones are two technologies that drive smart home adoption.

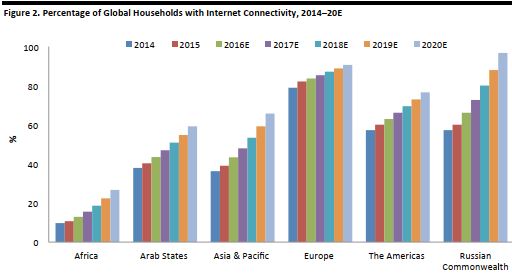
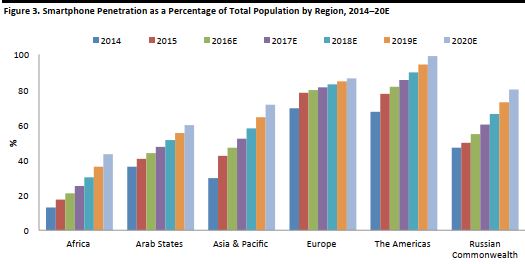
Based on data from the UN’s ITU agency, we predict that the worldwide percentage of households with Internet will touch 69% by 2020. We further estimate that global smartphone penetration will reach 75% in 2020, although the proportion of households with Internet connectivity and smartphones will be lower in developing countries.
We examined some key barriers to smart home adoption and the two that stand out the most are interoperability of devices and vulnerability to cyber attacks. Currently, it seems like devices that run on the ZigBee and Z-Wave protocols have higher levels of interoperability and can work across a wider area. Devices that run on these protocols also consume less energy, and can be arranged flexibly in a home.
Devices that connect to other devices or the Internet, and those that can be controlled by another person, are prone to cyber attacks. The susceptibility of smart devices to hackers seems to be just a fraction of a larger issue. Recent events suggest that companies could be collecting and storing sensitive customer information, possibly without customers’ authorization or knowledge.
While barriers to adoption exist, there are several measures that IoT companies and device manufacturers are taking to increase the viability of connected-home products. Companies are making an effort to include more devices under a popular protocol’s umbrella of compatible products, and IoT security companies can make consumers less apprehensive by providing them with tools to help them secure their connected homes.
Has the Smart Home Come of Age?
When you think of a futuristic, fully automated home, you might picture several household gadgets working in harmony, like in
The Jetsons or
Back to the Future. But what if one machine cannot understand the others, and the devices clash when they try to communicate with you? To help consumers avoid that scenario, most makers of smart home products specifically state that their devices work with a specific platform, so consumers will know that they work well with other products in that family.
The IoT, smart homes and connected living were some of the key themes at the Consumer Electronics Show (CES 2016) this year. Home appliance companies are continually refining their products and incorporating the latest advances in connected technology, but what makes a product or brand successful, and what drives customers to make the switch to a smart home?
In the previous reports in this series, we examined the various segments of the connected-home market. We looked at different gadgets and the features that distinguish them as smart products. In this concluding report, we recap some of the smart home market drivers, explore the barriers to adoption and offer some thoughts on the future of the connected home.
SMART HOME MARKET SET TO QUADRUPLE BY 2020
The global smart home market was valued at $9.8 billion in 2015, according to a study by Statista on the outlook for global digital markets, and it is estimated to reach $43.0 billion in 2020. In the race to dominate the IoT, companies are doing everything they can to stay ahead of the game. For example, Samsung announced at last year’s CES that 90% of the products it manufactures will be able to connect to the Internet by 2017.
[caption id="attachment_90908" align="aligncenter" width="354"]
 Source: Statista
Source: Statista[/caption]
Household Internet connectivity and smartphones are two technologies that drive smart home adoption. In order for users to remotely monitor and control their smart home devices, and for vendors and manufacturers to provide over-the-air maintenance updates, these technologies are essential.
Based on data from the UN’s ITU agency, we predict that the worldwide percentage of households with Internet will average 69% by 2020. This is a basic forecast that does not consider the evolution of other technologies and economic trends, but there is no doubt that there is increasing demand for Internet connectivity globally.
The growth rate is higher in developing economies because fewer houses in those areas currently have Internet connectivity. The growth rate will slow, and eventually flatten, in developed countries, as a larger percentage of houses will already have Internet connectivity.
[caption id="attachment_90909" align="aligncenter" width="512"]
 Source: ITU/FBIC Global Retail & Technology
Source: ITU/FBIC Global Retail & Technology[/caption]
The mobile phone market has also has been growing steadily. Based on mobile broadband subscription data from the ITU, we think global smartphone penetration will reach an average of 75% in 2020. As with household Internet connectivity, we believe growth will be faster in developing countries, where the market is less saturated, than in developed countries, where there is already widespread use of smartphones.

[caption id="attachment_90911" align="aligncenter" width="525"]
 Source:ITU/FBIC Global Retail & Technology
Source:ITU/FBIC Global Retail & Technology[/caption]
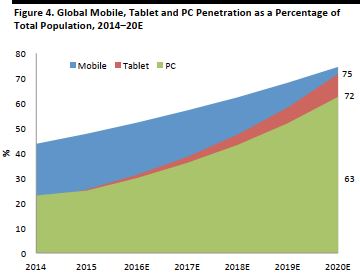
We think the global tablet penetration will be 72% and the PC penetration will be 63% by 2020. Since 2015, tablet sales and shipments have overtaken those of PCs.
Computer sales have slowed down considerably since the advent of portable, handheld devices, with consumers often preferring the latter for their convenience and affordability.
[caption id="attachment_90912" align="aligncenter" width="360"]
 Source: Credit Suisse/Gartner/eMarketer/ITU/FBIC Global Retail & Technology
Source: Credit Suisse/Gartner/eMarketer/ITU/FBIC Global Retail & Technology[/caption]
WHAT IS HOLDING BACK SMART HOME ADOPTION?
We examined some key barriers to smart home adoption in our first report, and the two that stand out the most are interoperability and vulnerability to cyber attacks. In this section, we explore these two constraints in detail.
Barrier 1: Interoperability
Interoperability in its basic sense means that different devices are able to interact and communicate with each other without special effort from the user. For example, if a home has a Nest thermostat, a Samsung washing machine and an Apple iPhone that can connect with each other easily, as if they were made by the same company, they are interoperable.
In order to communicate with each other effectively, the devices need to run on either the same protocol (or standard) or a protocol that can work with others. A protocol is a set of rules and conventions that allow two or more devices to exchange information. In a sense, a protocol is the “language” by which devices communicate.
Closed Versus Open Protocols
If a device made by one manufacturer is unable to interact with a device made by another, it is said to have a closed protocol. Devices that have an open protocol are able to communicate with each other, without any hindrance, irrespective of their manufacturers. Open protocols allow third-party developers free access, so they can create new products and applications that can be sold or licensed. A closed protocol will allow only the manufacturer of the product to develop more products and applications using that particular protocol.
Understandably, devices that run on open protocols will be more widely accepted in the market, as they do not require consumers to download multiple apps or install several hubs for all their devices to run smoothly. Protocol developers usually certify devices made by other manufacturers, so consumers can easily see whether a product will work with their existing setup or not.

Below, we highlight some of the most popular protocols used for home automation.
[caption id="attachment_90914" align="aligncenter" width="523"]
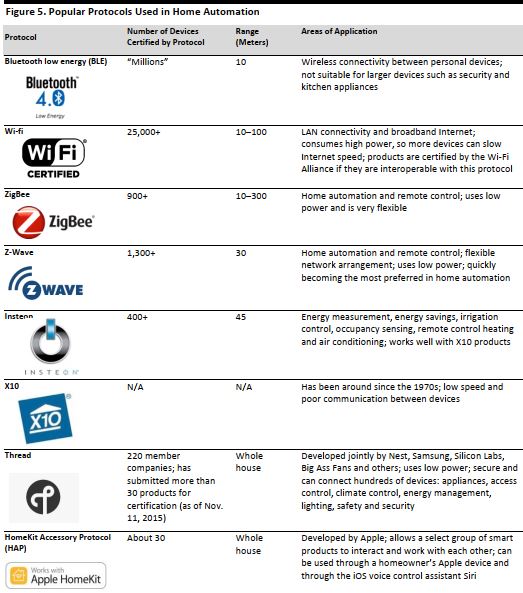 Source: Top Ten Reviews/Digital Trends/“Smart Home Communication Technologies and Applications: Wireless Protocol Assessment for Home Area Network Resources” by Tiago D. P. Mendes, Radu Godina, Eduardo M. G. Rodrigues, João C. O. Matias and João P. S. Catalão, published July 20, 2015, on www.mdpi.com/journal/energies/Threadgroup.org/Z-wavealliance.org/Bluetooth.com/Zigbee.com/ Apple.com/Insteon.com/FBIC Global Retail & Technology
Source: Top Ten Reviews/Digital Trends/“Smart Home Communication Technologies and Applications: Wireless Protocol Assessment for Home Area Network Resources” by Tiago D. P. Mendes, Radu Godina, Eduardo M. G. Rodrigues, João C. O. Matias and João P. S. Catalão, published July 20, 2015, on www.mdpi.com/journal/energies/Threadgroup.org/Z-wavealliance.org/Bluetooth.com/Zigbee.com/ Apple.com/Insteon.com/FBIC Global Retail & Technology[/caption]
Successful products will not only be compatible with several devices, but also able to work over a larger area, and they will consume less energy. Below, we examine what makes some of these protocols more popular than others.
Energy Consumption and Internet Speed
Numerous devices have Bluetooth and wi-fi capabilities, but these protocols do have their limitations: Bluetooth is not suitable for larger electronic devices and appliances, and wi-fi consumes more energy. Also, more devices working through wi-fi can slow the Internet connectivity in a home.
Effective Communication
Devices need to be able to communicate effectively with each other if everything is to work in sync in a connected home, but some protocols have limitations on this front. The X10 protocol seems dated and will not work with newer, high-tech gadgets. And Insteon has difficulty processing data quickly, which is necessary for such things as streaming video from a security camera—the video must stream in real time in order for the user to be able to take action instantly. In other words, Insteon has bandwidth limitations that make it unsuitable for home automation.
So Who Is the Winner?
Currently, it seems like devices that run on the ZigBee and Z-Wave protocols have higher levels of interoperability, and can work across a wider area. Devices that run on these protocols also consume less energy, and can be arranged flexibly in a home, meaning that the homeowner does not have to route all communications through a central hub in order for them to interact with each other.
Smart devices from Samsung, sold under the SmartThings brand, are capable of working with several products from other manufacturers that run on the Z-Wave, ZigBee and wi-fi/LAN protocols. Samsung is also collaborating with other companies to develop the Thread platform. One of the codevelopers of Thread is Nest, a Google company. We believe this collaboration, bolstered by Samsung’s expertise in home and consumer electronics, will result in stiff competition for Apple’s HomeKit platform.
Barrier 2: Vulnerability to Cyber Attacks
Devices that connect to other devices or the Internet, and those that can be controlled by another person, are prone to cyber attacks. Two recent cases highlight the vulnerability of smart devices.
Nest Thermostat Bug Turns Off Heating
A December 2015 software update to the Nest Learning Thermostat caused it to turn off heat and left users feeling cold—and understandably angry. The thermostat can adapt a house’s heating (and cooling) according to the user’s preferences and outside weather, without the user having to adjust it often. The pricey device’s failure, which was covered by the media, could make some would-be adopters think twice about switching to smart home technologies.
Hacker Obtains Children’s Photos, Personal Data from Smart Toys
In early November 2015, it was reported that a hacker had managed to gain access to millions of photos and other personal data by hacking Hong Kong–based VTech’s smart toys. The company’s technology allows parents to use a smartphone app to chat with their children through a VTech tablet. By snooping around the company’s servers, the hacker found nearly 190 GB worth of photos and messages that had been exchanged between parents and children.
The susceptibility of smart devices to hackers seems to be just a fraction of a larger issue. Events such as these suggest that companies could be collecting and storing sensitive customer information, possibly without customers’ authorization or knowledge. Once a smart product’s weakness to cyber attacks is exposed, the manufacturer usually releases a software updates or bug fix to remedy the problem. But is there a preventive measure that homeowners can take instead of waiting for a cure from a company that could prove too little too late?
SecuriThings, an IoT Security Platform
SecuriThings is an Israel-based firm that provides IoT security services. It was founded by security experts Roy Dagan and Raanan Lidji. Dagan spoke to us to shed some light on how homeowners can benefit from having an added layer of security.
What Is It?
SecuriThings is a security platform that is built into device manufacturers’ apps to provide an added security layer to a smart home’s network. With fee-based services, SecuriThings provides insight and analytics on the usage patterns of a home’s connected devices.
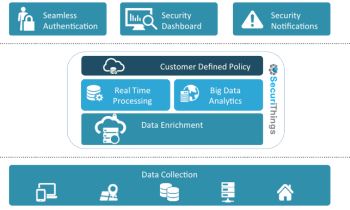
How Does It Work?
The platform analyzes a homeowner’s typical behavior in terms of app usage for the connected devices, and stores the information. If it identifies anomalies from the homeowner’s usual pattern, it flags them, as they could mean the home’s network has been threatened. For example, the security platform stores and analyzes the location where a homeowner uses each app and the usual times at which it is used. If the platform identifies a region that has not been in the usage history, it alerts the homeowner immediately. If the owner is traveling, he or she can turn off the notification or inform SecuriThings that there is no need for alarm.
Why Is It Necessary to Have an Added Layer of Security?
Dagan told us about how the smart home market has transformed over time. Previously, a vendor would install and hardwire all the devices/machines in a house, but these days, do-it-yourselfers reign. Dagan outlined how this has contributed to the vulnerability of a connected home’s security:
- Because the customer buys products from various shops and manufacturers, and sets up the connected-device network him- or herself, it is likely that the devices do not all have the same level of built-in security.
- Once the customer connects all the devices and sets up the network, information is constantly being stored, either on the devices or in a cloud (a shared storage and applications system accessed via the Internet).
- Most devices come with a static or default user name and password, which the customer often leaves unchanged.
- Seasoned hackers can easily gain access to these user names and passwords by snooping around the homeowner’s Internet history or through a brute-force attack that swiftly runs all the permutations and combinations of possible passwords.
Dagan added that when cyber attacks take place, device manufacturers often do not know or cannot detect the location of either the hacker or the breach. SecuriThings’ behavior-based security platform is able to identify when someone is attempting to access an app outside the user’s usual pattern, and it mitigates the risk of an attack with its unique user-identity accreditation tools.
THE FUTURE OF THE CONNECTED HOME
While barriers to adoption, such as interoperability and vulnerability to cyber attacks, exist, there are several measures that IoT companies and device manufacturers are taking to increase the viability of connected-home products. As we have outlined, companies are making an effort to include more devices under a popular protocol’s umbrella of compatible products. This will help customers operate their devices seamlessly. And IoT security companies, such as SecuriThings, can make consumers less apprehensive by providing them with tools to help them secure their connected homes.

 Based on data from the UN’s ITU agency, we predict that the worldwide percentage of households with Internet will touch 69% by 2020. We further estimate that global smartphone penetration will reach 75% in 2020, although the proportion of households with Internet connectivity and smartphones will be lower in developing countries.
We examined some key barriers to smart home adoption and the two that stand out the most are interoperability of devices and vulnerability to cyber attacks. Currently, it seems like devices that run on the ZigBee and Z-Wave protocols have higher levels of interoperability and can work across a wider area. Devices that run on these protocols also consume less energy, and can be arranged flexibly in a home.
Devices that connect to other devices or the Internet, and those that can be controlled by another person, are prone to cyber attacks. The susceptibility of smart devices to hackers seems to be just a fraction of a larger issue. Recent events suggest that companies could be collecting and storing sensitive customer information, possibly without customers’ authorization or knowledge.
While barriers to adoption exist, there are several measures that IoT companies and device manufacturers are taking to increase the viability of connected-home products. Companies are making an effort to include more devices under a popular protocol’s umbrella of compatible products, and IoT security companies can make consumers less apprehensive by providing them with tools to help them secure their connected homes.
Based on data from the UN’s ITU agency, we predict that the worldwide percentage of households with Internet will touch 69% by 2020. We further estimate that global smartphone penetration will reach 75% in 2020, although the proportion of households with Internet connectivity and smartphones will be lower in developing countries.
We examined some key barriers to smart home adoption and the two that stand out the most are interoperability of devices and vulnerability to cyber attacks. Currently, it seems like devices that run on the ZigBee and Z-Wave protocols have higher levels of interoperability and can work across a wider area. Devices that run on these protocols also consume less energy, and can be arranged flexibly in a home.
Devices that connect to other devices or the Internet, and those that can be controlled by another person, are prone to cyber attacks. The susceptibility of smart devices to hackers seems to be just a fraction of a larger issue. Recent events suggest that companies could be collecting and storing sensitive customer information, possibly without customers’ authorization or knowledge.
While barriers to adoption exist, there are several measures that IoT companies and device manufacturers are taking to increase the viability of connected-home products. Companies are making an effort to include more devices under a popular protocol’s umbrella of compatible products, and IoT security companies can make consumers less apprehensive by providing them with tools to help them secure their connected homes.
 Source: Statista[/caption]
Household Internet connectivity and smartphones are two technologies that drive smart home adoption. In order for users to remotely monitor and control their smart home devices, and for vendors and manufacturers to provide over-the-air maintenance updates, these technologies are essential.
Based on data from the UN’s ITU agency, we predict that the worldwide percentage of households with Internet will average 69% by 2020. This is a basic forecast that does not consider the evolution of other technologies and economic trends, but there is no doubt that there is increasing demand for Internet connectivity globally.
The growth rate is higher in developing economies because fewer houses in those areas currently have Internet connectivity. The growth rate will slow, and eventually flatten, in developed countries, as a larger percentage of houses will already have Internet connectivity.
[caption id="attachment_90909" align="aligncenter" width="512"]
Source: Statista[/caption]
Household Internet connectivity and smartphones are two technologies that drive smart home adoption. In order for users to remotely monitor and control their smart home devices, and for vendors and manufacturers to provide over-the-air maintenance updates, these technologies are essential.
Based on data from the UN’s ITU agency, we predict that the worldwide percentage of households with Internet will average 69% by 2020. This is a basic forecast that does not consider the evolution of other technologies and economic trends, but there is no doubt that there is increasing demand for Internet connectivity globally.
The growth rate is higher in developing economies because fewer houses in those areas currently have Internet connectivity. The growth rate will slow, and eventually flatten, in developed countries, as a larger percentage of houses will already have Internet connectivity.
[caption id="attachment_90909" align="aligncenter" width="512"] Source: ITU/FBIC Global Retail & Technology[/caption]
The mobile phone market has also has been growing steadily. Based on mobile broadband subscription data from the ITU, we think global smartphone penetration will reach an average of 75% in 2020. As with household Internet connectivity, we believe growth will be faster in developing countries, where the market is less saturated, than in developed countries, where there is already widespread use of smartphones.
Source: ITU/FBIC Global Retail & Technology[/caption]
The mobile phone market has also has been growing steadily. Based on mobile broadband subscription data from the ITU, we think global smartphone penetration will reach an average of 75% in 2020. As with household Internet connectivity, we believe growth will be faster in developing countries, where the market is less saturated, than in developed countries, where there is already widespread use of smartphones.
 [caption id="attachment_90911" align="aligncenter" width="525"]
[caption id="attachment_90911" align="aligncenter" width="525"] Source:ITU/FBIC Global Retail & Technology[/caption]
We think the global tablet penetration will be 72% and the PC penetration will be 63% by 2020. Since 2015, tablet sales and shipments have overtaken those of PCs.
Computer sales have slowed down considerably since the advent of portable, handheld devices, with consumers often preferring the latter for their convenience and affordability.
[caption id="attachment_90912" align="aligncenter" width="360"]
Source:ITU/FBIC Global Retail & Technology[/caption]
We think the global tablet penetration will be 72% and the PC penetration will be 63% by 2020. Since 2015, tablet sales and shipments have overtaken those of PCs.
Computer sales have slowed down considerably since the advent of portable, handheld devices, with consumers often preferring the latter for their convenience and affordability.
[caption id="attachment_90912" align="aligncenter" width="360"] Source: Credit Suisse/Gartner/eMarketer/ITU/FBIC Global Retail & Technology[/caption]
Source: Credit Suisse/Gartner/eMarketer/ITU/FBIC Global Retail & Technology[/caption]
 Below, we highlight some of the most popular protocols used for home automation.
[caption id="attachment_90914" align="aligncenter" width="523"]
Below, we highlight some of the most popular protocols used for home automation.
[caption id="attachment_90914" align="aligncenter" width="523"] Source: Top Ten Reviews/Digital Trends/“Smart Home Communication Technologies and Applications: Wireless Protocol Assessment for Home Area Network Resources” by Tiago D. P. Mendes, Radu Godina, Eduardo M. G. Rodrigues, João C. O. Matias and João P. S. Catalão, published July 20, 2015, on www.mdpi.com/journal/energies/Threadgroup.org/Z-wavealliance.org/Bluetooth.com/Zigbee.com/ Apple.com/Insteon.com/FBIC Global Retail & Technology[/caption]
Successful products will not only be compatible with several devices, but also able to work over a larger area, and they will consume less energy. Below, we examine what makes some of these protocols more popular than others.
Source: Top Ten Reviews/Digital Trends/“Smart Home Communication Technologies and Applications: Wireless Protocol Assessment for Home Area Network Resources” by Tiago D. P. Mendes, Radu Godina, Eduardo M. G. Rodrigues, João C. O. Matias and João P. S. Catalão, published July 20, 2015, on www.mdpi.com/journal/energies/Threadgroup.org/Z-wavealliance.org/Bluetooth.com/Zigbee.com/ Apple.com/Insteon.com/FBIC Global Retail & Technology[/caption]
Successful products will not only be compatible with several devices, but also able to work over a larger area, and they will consume less energy. Below, we examine what makes some of these protocols more popular than others.

